
Web filtering solutions involve monitoring and filtering internet traffic to prevent users from accessing specific websites, applications, or types of content that may be deemed inappropriate, unsafe, or non-compliant with organizational guidelines.
In today’s digital era, where Internet access is pervasive and essential for personal and professional purposes, ensuring a secure and productive online environment has become paramount.
Web filtering solutions are crucial in managing and controlling internet usage, allowing organizations to safeguard their networks, protect sensitive information, enforce acceptable use policies, and optimize productivity.
Web filtering software is designed to monitor and filter internet traffic, enabling organizations to control access to websites, applications, and content based on predefined rules and policies.
These solutions employ various techniques such as URL filtering, keyword filtering, category-based filtering, and content analysis to determine the appropriateness and safety of web content.
By implementing effective web filtering solutions, businesses can mitigate risks associated with cyber threats, prevent unauthorized access to malicious or inappropriate websites, and reduce the potential impact of phishing attacks, malware infections, data breaches, and compliance violations.
Furthermore, best web filtering solutions help organizations optimize bandwidth usage by restricting access to non-business-related websites, streaming platforms, or other resource-intensive applications.
Selecting the best web filtering Tools requires careful consideration of factors such as filtering accuracy, ease of deployment and management, scalability, reporting and analytics capabilities, integration with existing infrastructure, and compliance with industry regulations.
Organizations must assess their requirements and choose a solution that aligns with their objectives, industry regulations, and workforce needs.
What is Web Filtering?
Web filtering refers to controlling and managing access to websites and online content based on predetermined rules and policies.
Web filtering can be implemented at different levels, such as network, device, or browser. It typically involves filtering technologies and techniques to analyze URLs, web content, keywords, categories, and other attributes to determine whether a website or content should be allowed or blocked.
How Do Web Filtering Solutions Work?
Web filtering solutions are tools or systems for controlling and managing access to websites and online content. They are widely used in businesses, schools, and homes to enforce acceptable use restrictions, protect against malware and phishing, and assure regulatory compliance. The specifics of web filtering solutions vary based on the product or service provider. However, the following are the main steps:
URL Categorization: Most web filtering programs keep a large database of categorized URLs. Websites are categorized into several categories, including social media, gaming, adult content, news, and so on.
Filtering Policies: Administrators or users define filtering policies that govern which websites or content are permitted or prohibited. These restrictions can be based on specific URLs, keywords, or other criteria. Different filtering levels or profiles can be created for different user groups or devices.
Analysis and Decision Making: The web filtering solution compares the requested URL or content to its database and filtering policies. It determines whether the website fits into any restricted categories or matches any restricted criteria.
Real-Time Updates: To keep up with the ever-changing nature of the web, web filtering solutions frequently update their database and policies in real time. This includes adding new websites to good categories, deleting incorrectly classified sites, and remaining current on developing dangers.
Many web filtering solutions include extra capabilities like malware detection and prevention, phishing protection, bandwidth control, reporting and analytics, and SSL decryption to analyze encrypted data.
What are Web Filtering Solutions?
There are various sorts of web filtering solutions available, such as:
DNS-Based Filtering: These solutions limit access to specified websites based on their domain names or IP addresses at the DNS (Domain Name System) level.
Proxy-Based Filtering: Web traffic is intercepted and filtered using proxy servers. Users must connect to the proxy server, which filters and restricts their internet access according to established rules.
URL Filtering entails keeping a database of categorized URLs and comparing the requested URLs to this database. Access is forbidden if a requested URL matches a restricted category.
Keyword Filtering: Web filtering systems can restrict or allow access to websites based on the presence or absence of specific keywords in the content or URL of the website.
Content Analysis: These solutions scan website content and decide its suitability based on established policies using powerful algorithms and machine learning approaches.
Web Filtering Solutions Advantages
Web filtering technologies have numerous advantages, including:
- Keeping users away from hazardous or unsuitable content.
- Restricting access to non-work-related websites improves productivity.
- Blocking access to harmful websites to prevent malware and phishing assaults.
- Meeting legal or regulatory criteria.
- Allowing parents to keep their children away from inappropriate content.
Best Web Filtering Solutions and Features
| Best Web Filtering Solutions | Features |
|---|---|
| 1. Perimeter81 | 1. Secure Network Access 2. Zero Trust Architecture 3. Software-Defined Perimeter 4. Cloud VPN 5. Multi-Factor Authentication 6. Network Segmentation 7. Threat Intelligence Integration 8. Centralized Management 9. User Activity Monitoring 10. Secure Web Gateway |
| 2. Cisco Umbrella | 1. Cloud-based Security 2. Secure Web Gateway 3. URL Filtering 4. Advanced Threat Protection 5. Data Loss Prevention 6. Cloud Application Control 7. SSL Inspection 8. User and Device Authentication 9. Policy-based Access Control 10. Content Filtering |
| 3. Zscaler Internet Access | 1. Web Content Filtering 2. Malware Protection 3. Application Control 4. SSL Inspection 5. User Authentication 6. Bandwidth Management 7. Reporting and Analytics 8. Virus and Spyware Protection 9. URL Filtering 10. Cloud-based Management |
| 4. Symantec WebFilter | 1. Web Content Filtering 2. Advanced Threat Protection 3. Data Loss Prevention 4. SSL Inspection 5. Application Control 6. User Authentication 7. Malware Protection 8. URL Filtering 9. Reporting and Analytics |
| 5. Barracuda Web Security Gateway | 1. Web content filtering 2. Malware and virus protection 3. SSL inspection 4. Application control 5. User authentication and policy enforcement 6. Bandwidth management and QoS 7. Reporting and analytics 8. Mobile and remote filtering |
| 6. Forcepoint Web Security | 1. Web Content Filtering 2. Malware Protection 3. SSL Inspection 4. URL Filtering 5. Application Control 6. Data Loss Prevention 7. User Authentication 8. Reporting and Analytics 9. Bandwidth Management |
| 7. McAfee Web Gateway |
1. Web Content Filtering 2. Malware Protection 3. URL Filtering 4. Application Control 5. SSL Inspection 6. Data Loss Prevention 7. User Authentication 8. Reporting and Analytics 9. Bandwidth Management 10. Cloud-based Management |
| 8. Sophos Web Appliance | 1. URL Categorization 2. Malicious URL Detection 3. Application-based Filtering 4. Custom URL Filtering Policies 5. SSL Inspection 6. User Authentication 7. Reporting and Logging 8. Granular Policy Control 9. Real-time Threat Intelligence |
| 9. Palo Alto Networks URL Filtering |
1. Web Content Filtering 2. SSL Inspection 3. Malware Protection 4. URL Filtering 5. Application Control 6. Data Loss Prevention 7. User Authentication 8. Reporting and Analytics |
| 10. Smoothwall Web Filter |
1. Web Content Filtering 2. URL Filtering 3. Malware Protection 4. Application Control 5. User Authentication 6. Reporting and Analytics 7. Bandwidth Management 8. Time-based Policies 10. Custom Blacklists and Whitelists |
| 11. iBoss Web Security |
1. Application Control 2. User Authentication 3. Reporting and Logging 4. Bandwidth Management 5. Threat Intelligence Integration 6. Cloud-based Management 7. Mobile and Remote Filtering 8. Customizable Policies |
| 12. Fortinet FortiGate Web Filtering |
1. Web Content Filtering 2. URL Filtering 3. Malware Protection 4. Application Control 5. User Authentication 6. Reporting and Analytics 7. Bandwidth Management |
| 13. GFI WebMonitor | 1. Web content filtering 2. Malware and virus protection 3. SSL inspection 4. Application control 5. Bandwidth management 6. Real-time monitoring and reporting 7. User authentication and policy enforcement 8. Mobile device support |
| 14. OpenDNS |
1. Web Content Filtering 2. URL Filtering 3. Malware Protection 4. Application Control 5. User Authentication 6. Reporting and Analytics 7. Bandwidth Management |
| 15. Untangle Web Filter | 1. Application control 2. Bandwidth management 3. Reporting and analytics 4. User authentication and policy enforcement 5. URL categorization and blacklisting 6. Safe search enforcement 7. Active Directory integration. |
| 16. WebTitan | 1. Malware and phishing protection 2. SSL inspection 3. Application control 4. Bandwidth management 5. Reporting and analytics 6. User authentication and policy enforcement 7. URL categorization and blacklisting |
| 17. DNSFilter |
1. DNS filtering 2. Content filtering 3. Malware and phishing protection 4. Advanced threat intelligence 5. Reporting and analytics 6. Roaming protection 7. Granular policy control 8. Integration and API support |
| 18. McAfee Web Protection |
1. Malware and virus protection 2. SSL inspection 3. Application control 4. Data loss prevention (DLP) 5. Advanced threat defense 6. Reporting and analytics 7. User authentication and policy enforcement 8. Bandwidth management |
Best Web Filtering Solutions 2023
- Perimeter81
- Cisco Umbrella
- Zscaler Internet Access
- Symantec WebFilter
- Barracuda Web Security Gateway
- Forcepoint Web Security
- McAfee Web Gateway
- Sophos Web Appliance
- Palo Alto Networks URL Filtering
- Smoothwall Web Filter
- iBoss Web Security
- Fortinet FortiGate Web Filtering
- GFI WebMonitor
- OpenDNS
- Untangle Web Filter
- WebTitan
- DNSFilter
- McAfee Web Protection
The choice of the best web filtering solution depends on specific requirements, organizational needs, and industry regulations. However, here are some highly regarded web filtering solutions that have gained recognition for their features, capabilities, and effectiveness:
1. Perimeter81
Perimeter81 offers web filtering solutions as part of its network security platform.
These solutions provide organizations with control over internet access by filtering URLs, content, and applications.
It includes features like URL filtering, content filtering, malware and phishing protection, application control, reporting, and VPN and network security integration.
Perimeter81’s web filtering solutions enable organizations to enhance security, productivity, and compliance by managing and controlling web access effectively.
Features
- Secure Network Access: Provides secure and controlled access to network resources for remote and on-premises users.
- Zero Trust Architecture: Implements a zero-trust security model, requiring authentication and authorization for every access attempt.
- Software-Defined Perimeter: Utilizes software-defined networking to create a flexible and scalable security framework.
- Cloud VPN: Establishes secure connections between remote users and cloud resources, ensuring encrypted data transmission.
- Multi-Factor Authentication: Requires multiple authentication factors, such as passwords, biometrics, or tokens, for enhanced user verification.
- Network Segmentation: Divides the network into smaller segments, reducing the potential impact of security breaches and limiting lateral movement.
- Threat Intelligence Integration: Integrates with threat intelligence feeds to identify and mitigate potential security risks.
- Centralized Management: Offers a centralized platform for managing network access, policies, and user authentication, simplifying administration.
- User Activity Monitoring: Tracks and monitors user activity, enabling the detection of suspicious behavior and potential security breaches.
- Secure Web Gateway: Provides secure web browsing by filtering and inspecting web traffic for threats, malware, and unauthorized access attempts.
- Mobile Device Management: Offers device-level security controls and management for mobile devices, ensuring secure access and data protection.
- Auditing and Reporting: Generates comprehensive reports and logs for auditing purposes and compliance requirements, maintaining visibility into network activities.
Pros
- Comprehensive Security: Perimeter81 offers a range of security features, including web filtering, VPN, and network security, providing organizations with a holistic approach to protecting their networks and data.
- Easy Deployment and Management: Perimeter81’s cloud-based platform simplifies deployment and management, allowing organizations to quickly set up and configure their network security infrastructure without complex hardware or extensive IT resources.
- Scalability: Perimeter81 is designed to scale with the organization’s needs, accommodating growing network requirements and expanding user bases.
- User-friendly Interface: The platform provides a user-friendly interface that simplifies network management tasks, making it accessible to IT teams with varying levels of technical expertise.
- Secure Remote Access: Perimeter81’s VPN capabilities enable secure remote access to corporate resources, ensuring that remote employees can work safely and efficiently.
Cons
- Limited Feature Set: While Perimeter81 offers a comprehensive network security platform, certain advanced features in specialized solutions may be missing.
- Organizations with specific requirements may need to consider additional security solutions.
- Pricing: The cost of Perimeter81’s services may vary based on the organization’s needs, and it may be relatively higher compared to standalone solutions focused on a specific security aspect.
- Dependency on Internet Connectivity: Perimeter81’s cloud-based approach means organizations rely on stable and reliable Internet connectivity for their network security infrastructure to function optimally. Connectivity issues can impact accessibility and performance.
2. Cisco Umbrella

Cisco Umbrella is a cloud-based web filtering and security platform. It uses DNS to filter and block access to malicious or inappropriate websites.
It provides advanced threat protection, content filtering, and secure web gateway capabilities. Umbrella allows organizations to create custom policies, offers flexible deployment options, and integrates with the Cisco security ecosystem.
It helps protect against online threats, enforce web access policies, and enhance security.
Features
- DNS and IP-layer Security: Protects the DNS and IP layers, blocking connections to malicious sites and IPs.
- Web Filtering: Implements web content filtering to enforce acceptable use policies and block access to inappropriate or risky websites.
- Malware and Phishing Protection: Detects and blocks malware infections, including ransomware, and prevents phishing attacks.
- Secure Internet Gateway: Offers secure internet access for users, regardless of location, by redirecting traffic through Cisco Umbrella.
- Threat Intelligence: Utilizes extensive threat intelligence to identify and block known malicious domains, IPs, and URLs.
- Command and Control (C2) Callback Blocking: Prevents infected devices from communicating with command-and-control servers.
- Secure DNS: Protects against DNS-based attacks, such as DNS hijacking and DNS tunneling.
- Intelligent Proxy: Provides granular control over web traffic, allowing for policy enforcement and visibility into encrypted traffic.
- Roaming Protection: Extends security protection to roaming devices, even off the corporate network.
- Reporting and Analytics: Offer detailed reports on web activity, security events, and threat intelligence insights.
- Integration with Security Ecosystem: Integrates seamlessly with other Cisco security solutions and third-party products for enhanced protection.
- Cloud-based Management: Provides centralized management and policy enforcement across multiple locations and devices.
Pros
- Advanced Threat Protection: Cisco Umbrella incorporates a vast threat intelligence network, providing organizations with proactive protection against malware, phishing, and other online threats.
- Cloud-based Deployment: Cisco Umbrella offers easy and scalable deployment without complex hardware or software installations as a cloud-based solution.
- DNS-Based Filtering: By leveraging DNS, Umbrella can filter web traffic at the DNS level, allowing for quick and efficient blocking of malicious or inappropriate websites.
- Content Filtering and Policy Control: Umbrella enables organizations to create customized policies for web content filtering, giving them granular control over web access based on specific categories or individual websites.
- Integration with Cisco Security Ecosystem: Umbrella seamlessly integrates with other Cisco security solutions, providing a unified approach to network security and threat management.
Cons
- Cost: The pricing of Cisco Umbrella can be relatively higher compared to standalone web filtering solutions, particularly for smaller organizations or those with budget constraints.
- Limited Customization: While Cisco Umbrella offers a range of pre-defined content filtering categories, some organizations may require more specific or customized filtering options that may not be available.
- Dependency on Internet Connectivity: Cisco Umbrella relies on stable Internet connectivity as a cloud-based solution. Disruptions in internet connectivity can affect its ability to filter web traffic effectively.
- Learning Curve: Some users may require time to familiarize themselves with the features and administration interface of Cisco Umbrella, particularly if they are not already familiar with Cisco’s security ecosystem.
3. Zscaler Internet Access
Zscaler Internet Access is a cloud-native web filtering and security platform. It offers URL and content filtering, malware protection, application control, SSL inspection, and reporting capabilities.
The platform helps organizations enforce acceptable use policies, protect against web-based threats, and optimize internet access. Its cloud-native architecture ensures scalability and global coverage.
Zscaler Internet Access provides comprehensive web filtering solutions for enhanced security and control.
Features
- Cloud-based Security: Zscaler operates as a cloud-based security platform, providing security services without the need for on-premises hardware or appliances.
- Web Content Filtering: Implements robust web content filtering capabilities to enforce acceptable use policies and block access to inappropriate or malicious websites.
- URL Filtering: Blocks access to specific URLs or categories of websites based on customizable policies and predefined categories.
- Malware Protection: Detects and blocks known and unknown malware threats in real-time, ensuring the security of network and user devices.
- Secure Web Gateway: Acts as a secure web gateway, inspecting web traffic for threats and protecting against malicious downloads and phishing attacks.
- Data Loss Prevention (DLP): Prevents sensitive data from leaving the network through web-based channels, ensuring data protection and compliance.
- SSL Inspection: Performs SSL/TLS inspection to decrypt and inspect encrypted traffic, providing visibility into potential threats hidden in encrypted communications.
- Cloud Application Control: Controls and secures access to cloud-based applications, ensuring policy enforcement and preventing unauthorized access.
- User and Device Authentication: Validates user and device identities to ensure secure access to internet resources, leveraging multi-factor authentication if desired.
- Reporting and Analytics: Offer detailed reports and analytics on web activity, user behavior, and security events for improved visibility and compliance.
- Bandwidth Management: Controls and optimizes internet bandwidth usage, ensuring a consistent user experience and efficient network utilization.
- Mobile and Remote Filtering: Extends security protection to mobile and remote users, regardless of their location or device, providing consistent policy enforcement.
Pros
- Cloud-Native Architecture: Being cloud-native, Zscaler Internet Access offers easy deployment, scalability, and global coverage without needing on-premises hardware or complex configurations.
- Comprehensive Web Filtering: The platform provides a wide range of web filtering capabilities, including URL filtering, content filtering, and application control, enabling organizations to enforce acceptable use policies effectively.
- Advanced Threat Protection: Zscaler Internet Access incorporates advanced threat intelligence and malware protection mechanisms, safeguarding users from web-based threats and malicious content.
- SSL Inspection: The platform supports SSL inspection, allowing organizations to inspect encrypted web traffic for threats and policy compliance, enhancing overall security.
- Reporting and Analytics: Zscaler Internet Access offers detailed reporting and analytics features, providing insights into web usage, blocked requests, and security events, helping organizations monitor user behavior and identify potential threats.
Cons
- Dependency on Internet Connectivity: Zscaler Internet Access relies on stable and reliable Internet connectivity as a cloud-based solution. Network disruptions or outages may impact the availability and performance of the web filtering capabilities.
- Learning Curve: Organizations may require some time and training to become familiar with the platform’s administration interface and advanced features, especially if they are new to cloud-native security solutions.
- Cost: The pricing of Zscaler Internet Access may vary based on the organization’s requirements and user count. It may be relatively higher than standalone web filtering solutions, especially for smaller organizations or those with budget constraints.
4. Symantec WebFilter
Symantec WebFilter is a web filtering solution offered by Symantec. It helps organizations protect their networks by controlling and filtering web access based on predefined policies.
It offers features such as content filtering, malware protection, bandwidth control, URL filtering, and reporting.
Symantec WebFilter ensures a secure and productive online environment by blocking malicious content, enforcing acceptable use policies, and providing insights into web usage.
Features
- Web Content Filtering: Filters web content based on predefined or custom policies to block access to inappropriate or malicious websites.
- URL Filtering: Controls access to specific URLs or categories of websites to enforce acceptable use policies and prevent access to unauthorized or high-risk sites.
- Malware Protection: Detects and blocks known and unknown malware threats, including viruses, ransomware, and spyware, from accessing the network.
- Application Control: Manages and controls access to web applications, allowing organizations to restrict or block specific applications based on policy requirements.
- SSL Inspection: Performs SSL/TLS decryption and inspection to detect and prevent threats hidden in encrypted traffic.
- User Authentication: Validates user identities through various authentication mechanisms to ensure secure access to web resources and prevent unauthorized access.
- Reporting and Analytics: Provides detailed reports and analytics on web usage, user activities, and security events for better visibility and compliance monitoring.
- Bandwidth Management: Optimizes network bandwidth usage by controlling and prioritizing web traffic, ensuring optimal performance for critical applications.
- Mobile and Remote Filtering: Extends web filtering and security policies to mobile and remote users, ensuring consistent protection across different environments.
- Policy Customization: Allows organizations to define and customize web filtering policies based on their specific requirements and compliance needs.
- Real-time Threat Intelligence: Integrates with threat intelligence feeds to stay updated on the latest threats and provide proactive protection against emerging risks.
- Centralized Management: Provides a centralized management console for easy administration, policy configuration, and monitoring of web security across the network.
Pros
- Comprehensive Web Filtering: Symantec WebFilter offers a range of web filtering capabilities, including content filtering, URL filtering, and bandwidth control, allowing organizations to enforce acceptable use policies effectively.
- Malware Protection: The solution incorporates real-time threat intelligence to detect and block access to websites hosting malware, protecting users from potential security risks.
- Reporting and Monitoring: Symantec WebFilter provides reporting and monitoring features, giving administrators insights into web usage, blocked requests, and security events, helping them identify risks, and ensuring policy compliance.
- Integration with Symantec Security Solutions: Symantec WebFilter integrates with other Symantec security solutions, creating a unified approach to network security and enabling enhanced threat visibility and response.
Cons
- Limited Customization: Symantec WebFilter may have limited flexibility in terms of customization, especially when compared to specialized or standalone web Content filtering solutions that offer more granular control over filtering rules and categories.
- Complexity for Large Deployments: Managing and configuring Symantec WebFilter for large-scale deployments can be complex and time-consuming, requiring careful planning and coordination.
- On-Premises Deployment: Symantec WebFilter typically requires on-premises deployment, which may require additional hardware, software, and maintenance resources for organizations with limited IT infrastructure or those preferring cloud-based solutions.
5. Barracuda Web Security Gateway
The Barracuda Web Security Gateway is a web filtering and security solution provided by Barracuda Networks.
It offers features such as web content filtering, malware protection, application control, SSL inspection, and reporting.
The solution helps organizations enforce acceptable use policies, protect against web-based threats, and gain insights into web usage. It ensures a secure and productive web browsing environment for users.
Features
- Web Content Filtering: Filters web content based on categories and custom policies to enforce acceptable use policies and block access to inappropriate websites.
- Malware Protection: Detects and blocks known and zero-day malware threats, including viruses, ransomware, and spyware, preventing them from entering the network.
- Application Control: Controls access to web applications, allowing organizations to define policies and restrict or block specific applications based on their requirements.
- SSL Inspection: Performs SSL/TLS decryption and inspection to identify and prevent threats hidden in encrypted web traffic.
- User Authentication: Validates user identities through various authentication methods, such as LDAP integration or single sign-on (SSO), ensuring secure access to web resources.
- Reporting and Analytics: Provide detailed reports and analytics on web usage, user activities, and security events for compliance monitoring and better visibility.
- URL Filtering: Controls access to specific URLs or categories of websites, allowing organizations to enforce web browsing policies and prevent access to high-risk sites.
- Bandwidth Management: Manages and optimizes network bandwidth usage by controlling and prioritizing web traffic, ensuring optimal performance for critical applications.
- Mobile and Remote Filtering: Extends web filtering and security policies to mobile and remote users, providing consistent protection across different environments.
- Safe Search Enforcement: Enforces safe search policies on popular search engines to prevent users from accessing explicit or inappropriate search results.
- Data Loss Prevention (DLP): Prevents the unauthorized transmission of sensitive data through web channels, protecting confidential information.
- Cloud-based Management: Provides a centralized management console accessible from anywhere, allowing administrators to easily configure policies, monitor activity, and apply updates.
Pros
- Comprehensive Web Filtering: Barracuda Web Security Gateway offers a wide range of web filtering capabilities, allowing organizations to enforce acceptable use policies and protect against malicious or inappropriate content.
- Malware Protection: The solution incorporates advanced threat intelligence and malware scanning, providing robust protection against web-based threats.
- Application Control: Barracuda Web Security Gateway enables organizations to control and monitor access to web applications, helping improve productivity and mitigate security risks associated with unauthorized application usage.
- SSL Inspection: The solution supports SSL inspection, allowing organizations to inspect encrypted web traffic for threats and policy compliance, enhancing overall security.
- Reporting and Analytics: Barracuda Web Security Gateway provides comprehensive reporting and analytics features, offering insights into web usage, blocked requests, and security events. This helps organizations monitor user behavior and ensure policy compliance.
Cons
- Complexity for Large Deployments: Configuring and managing Barracuda Web Security Gateway for large-scale deployments can be complex and time-consuming, requiring careful planning and coordination.
- On-Premises Deployment: The solution typically requires on-premises deployment, which may require additional hardware, software, and maintenance resources for organizations with limited IT infrastructure or those preferring cloud-based solutions.
- Learning Curve: Administrators may require time and training to become familiar with the solution’s administration interface and advanced features.
6. Forcepoint Web Security
Forcepoint Web Security is a web filtering and security solution provided by Forcepoint. It helps organizations protect their networks by filtering web content, blocking malicious websites, and enforcing acceptable use policies.
It offers web content filtering, threat protection, application control, SSL inspection, and reporting features.
Forcepoint Web Security ensures a secure web browsing environment, helps mitigate web-based threats, and provides insights into web activity.
Features
- Web Content Filtering: Filters web content based on policies and categories to enforce acceptable use policies and block access to inappropriate or malicious websites.
- Advanced Threat Protection: Uses advanced threat detection techniques, including sandboxing and behavioral analysis, to identify and block sophisticated malware and zero-day threats.
- Data Loss Prevention (DLP): Prevents the unauthorized transmission of sensitive data through web channels, ensuring compliance with data protection regulations.
- SSL/TLS Inspection: Decrypts and inspects encrypted web traffic to detect and prevent threats hidden within SSL/TLS connections.
- Application Control: Controls access to web applications, allowing organizations to define policies and restrict or block specific applications based on their requirements.
- User Authentication: Validates user identities through various authentication methods, such as Active Directory integration or single sign-on (SSO), ensuring secure access to web resources.
- Reporting and Analytics: Provide detailed reports and analytics on web usage, user activities, and security events for compliance monitoring and better visibility into web traffic.
- URL Filtering: Controls access to specific URLs or categories of websites, allowing organizations to enforce web browsing policies and prevent access to high-risk sites.
- Threat Intelligence Integration: Incorporates threat intelligence feeds and real-time updates to identify and block known malicious websites, IPs, and domains.
- Mobile and Remote Filtering: Extends web filtering and security policies to mobile and remote users, ensuring consistent protection across different environments.
- Cloud-based Management: Offers centralized cloud-based management for easy policy configuration, monitoring, and updates across distributed environments.
- Bandwidth Management: Manages and optimizes network bandwidth usage by controlling and prioritizing web traffic, ensuring optimal performance for critical applications.
Pros
- Comprehensive Web Filtering: Forcepoint Web Security offers extensive web filtering capabilities, allowing organizations to control and filter web content based on categories, URLs, or keywords, ensuring compliance with acceptable use policies.
- Threat Protection: The solution incorporates advanced threat intelligence and real-time scanning, providing robust protection against web-based threats such as malware, phishing, and other malicious content.
- Application Control: Forcepoint Web Security enables organizations to manage and monitor access to web applications, allowing for granular control over application usage and helping enforce productivity and security policies.
- SSL Inspection: The solution supports SSL inspection, allowing organizations to inspect encrypted web traffic for threats and policy compliance, enhancing overall security.
- Reporting and Analytics: Forcepoint Web Security provides comprehensive reporting and analytics features, offering insights into web usage, blocked requests, and security events, aiding in monitoring user behavior, and identifying potential risks.
Cons
- Complexity for Configuration: Configuring and managing Forcepoint Web Security may require expertise and time, especially for larger deployments or complex network environments.
- On-Premises Deployment: The solution typically requires on-premises deployment, which may involve additional hardware, software, and maintenance resources, especially for organizations with limited IT infrastructure or those preferring cloud-based solutions.
- Learning Curve: Administrators may need some time to become familiar with the solution’s administration interface and advanced features, particularly if they are new to Forcepoint Web Security or similar security solutions.
7. McAfee Web Gateway
McAfee Web Gateway is a web filtering and security solution provided by McAfee.
It helps organizations protect their networks by controlling and monitoring web traffic, blocking harmful websites, and enforcing usage policies.
It offers features like web content filtering, threat protection, SSL inspection, application control, and reporting.
McAfee Web Gateway ensures users a safe and productive web browsing experience by filtering out malicious content and managing access to web applications.
Features
- Web Content Filtering: Filters web content based on policies and categories to enforce acceptable use policies and block access to inappropriate or malicious websites.
- Malware Protection: Detects and blocks known and unknown malware threats, including viruses, ransomware, and spyware, preventing them from entering the network.
- SSL/TLS Inspection: Performs SSL/TLS decryption and inspection to identify and prevent threats hidden within encrypted web traffic.
- Advanced Threat Detection: Utilizes advanced techniques, such as sandboxing and behavioral analysis, to detect and block sophisticated malware and zero-day threats.
- Data Loss Prevention (DLP): Prevents the unauthorized transmission of sensitive data through web channels, ensuring compliance with data protection regulations.
- Application Control: Controls access to web applications, allowing organizations to define policies and restrict or block specific applications based on their requirements.
- User Authentication: Validates user identities through various authentication methods, such as Active Directory integration or single sign-on (SSO), ensuring secure access to web resources.
- Reporting and Analytics: Provide detailed reports and analytics on web usage, user activities, and security events for compliance monitoring and better visibility into web traffic.
- URL Filtering: Controls access to specific URLs or categories of websites, allowing organizations to enforce web browsing policies and prevent access to high-risk sites.
- Mobile and Remote Filtering: Extends web filtering and security policies to mobile and remote users, ensuring consistent protection across different environments.
- Cloud-based Management: Offers centralized cloud-based management for easy policy configuration, monitoring, and updates across distributed environments.
- Bandwidth Management: Manages and optimizes network bandwidth usage by controlling and prioritizing web traffic, ensuring optimal performance for critical applications.
Pros
- Robust Web Filtering: McAfee Web Gateway offers comprehensive web filtering capabilities, allowing organizations to control and monitor web traffic based on categories, URLs, or keywords, ensuring compliance with usage policies.
- Threat Protection: The solution includes advanced threat intelligence and real-time scanning, protecting against malware, phishing attacks, and other web-based threats.
- SSL Inspection: McAfee Web Gateway supports SSL inspection, allowing organizations to inspect encrypted web traffic for potential threats and policy compliance.
- Application Control: The solution enables organizations to manage and monitor access to web applications, helping enforce productivity and security policies.
- Reporting and Analytics: McAfee Web Gateway provides detailed reporting and analytics, offering insights into web usage, blocked requests, and security events, aiding in monitoring and compliance efforts.
Cons
- Complex Configuration: Setting up and managing McAfee Web Gateway may require technical expertise and time, especially for larger deployments or complex network environments.
- Resource Intensive: Depending on the deployment model, the solution may require dedicated hardware or virtual machine resources, which could be a consideration for organizations with limited infrastructure.
- Learning Curve: Administrators may need time to become familiar with the administration interface and advanced features of McAfee Web Gateway.
8. Sophos Web Appliance
Sophos Web Appliance is a web filtering and security solution provided by Sophos. It helps organizations protect their networks by filtering web content, blocking malicious websites, and enforcing acceptable use policies.
The solution includes features such as web content filtering, malware protection, application control, reporting, and bandwidth management.
Sophos Web Appliance ensures a secure web browsing environment, mitigates web-based threats, and provides insights into web activity for organizations.
Features
- Web Content Filtering: Filters web content based on policies and categories to enforce acceptable use policies and block access to inappropriate or malicious websites.
- Malware Protection: Detects and blocks known and unknown malware threats, including viruses, ransomware, and spyware, preventing them from entering the network.
- SSL/TLS Inspection: Decrypts and inspects encrypted web traffic to identify and prevent threats hidden within SSL/TLS connections.
- Advanced Threat Protection: Utilizes advanced techniques, such as sandboxing and behavioral analysis, to detect and block sophisticated malware and zero-day threats.
- Application Control: Controls access to web applications, allowing organizations to define policies and restrict or block specific applications based on their requirements.
- Data Loss Prevention (DLP): Prevents the unauthorized transmission of sensitive data through web channels, ensuring compliance with data protection regulations.
- User Authentication: Validates user identities through various authentication methods, such as Active Directory integration or single sign-on (SSO), ensuring secure access to web resources.
- Reporting and Analytics: Provides detailed reports and analytics on web usage, user activities, and security events for compliance monitoring and better visibility into web traffic.
- URL Filtering: Controls access to specific URLs or categories of websites, allowing organizations to enforce web browsing policies and prevent access to high-risk sites.
- Mobile and Remote Filtering: Extends web filtering and security policies to mobile and remote users, ensuring consistent protection across different environments.
- Bandwidth Management: Manages and optimizes network bandwidth usage by controlling and prioritizing web traffic, ensuring optimal performance for critical applications.
- Cloud-based Management: Offers centralized cloud-based management for easy policy configuration, monitoring, and updates across distributed environments.
Pros
- Robust Web Filtering: Sophos Web Appliance offers extensive web filtering capabilities, allowing organizations to control and monitor web content based on categories, URLs, or specific keywords. It helps enforce acceptable use policies and protects against malicious or inappropriate websites.
- Malware Protection: The solution incorporates advanced threat detection technologies, protecting against web-based threats such as malware and phishing attempts. It helps safeguard users from potential security risks.
- Application Control: Sophos Web Appliance enables organizations to control and manage access to web applications, allowing administrators to define policies and restrict usage based on categories or specific applications. It helps improve productivity and mitigate security risks associated with unauthorized application usage.
- Reporting and Logging: The solution provides comprehensive reporting and logging features, offering insights into web activity, user behavior, blocked requests, and security events. This helps organizations monitor web usage, identify potential risks, and maintain compliance with web access policies.
- Bandwidth Management: Sophos Web Appliance includes bandwidth management capabilities, allowing organizations to prioritize or limit bandwidth usage for different web categories or applications. It helps optimize network performance and ensure a smooth browsing experience for users.
Cons
- Initial Configuration Complexity: Setting up and configuring Sophos Web Appliance may require technical expertise and time, especially for larger deployments or complex network environments.
- Resource Requirements: Depending on the deployment model, the solution may require dedicated hardware or virtual machine resources, which could be a consideration for organizations with limited infrastructure.
- Learning Curve: Administrators may need time to become familiar with the administration interface and advanced features of Sophos Web Appliance.
9. Palo Alto Networks URL Filtering
Palo Alto Networks URL Filtering is a web security feature allowing organizations to control and filter website access based on URLs or categories.
It helps protect against web-based threats by blocking malicious or inappropriate websites.
The solution provides customization options, advanced threat prevention, and reporting capabilities to enhance web security and enforce acceptable use policies.
Palo Alto Networks URL Filtering allows organizations to manage and monitor web activity effectively.
Features
- Web Content Filtering: Filters web content based on policies and categories to enforce acceptable use policies and block access to inappropriate or malicious websites.
- Malware Protection: Detects and blocks known and unknown malware threats, including viruses, ransomware, and spyware, preventing them from entering the network.
- SSL Decryption: Decrypts and inspects SSL/TLS-encrypted web traffic to identify and prevent threats hidden within encrypted connections.
- Advanced Threat Protection: Utilizes advanced techniques, such as machine learning and behavioral analysis, to detect and block sophisticated malware and zero-day threats.
- User-Based Policies: Allows organizations to define policies based on user roles or groups, enabling granular control over web access and filtering.
- URL Filtering: Controls access to specific URLs or categories of websites, allowing organizations to enforce web browsing policies and prevent access to high-risk sites.
- Customizable Policies: Provides flexibility in creating custom policies to meet specific security and compliance requirements.
- Reporting and Analytics: Offer detailed reports and analytics on web usage, user activities, and security events for compliance monitoring and better visibility.
- Integration with Threat Intelligence: Incorporates threat intelligence feeds and real-time updates to identify and block known malicious websites, IPs, and domains.
- Mobile and Remote Filtering: Extends web filtering and security policies to mobile and remote users, ensuring consistent protection across different environments.
- Bandwidth Management: Manages and optimizes network bandwidth usage by controlling and prioritizing web traffic, ensuring optimal performance for critical applications.
- Cloud-based Management: Provides centralized cloud-based management for easy policy configuration, monitoring, and updates across distributed environments.
Pros
- Robust Web Filtering: Palo Alto Networks URL Filtering offers comprehensive web filtering capabilities, allowing organizations to control and filter website access based on URLs or category classifications. It helps enforce acceptable use policies and protects against malicious or inappropriate web content.
- Advanced Threat Prevention: The solution incorporates real-time scanning and advanced threat intelligence to identify and block access to websites hosting malware, phishing attempts, or other web-based threats. It provides strong protection against web-based security risks.
- Category-Based Filtering: Palo Alto Networks URL Filtering utilizes a vast database of categorized websites, enabling organizations to apply granular control over web access based on predefined categories. This allows for precise filtering and customization to align with specific security and compliance requirements.
- Customization and Flexibility: The solution offers customization options, allowing administrators to create exceptions, whitelist or blacklist specific URLs, and tailor filtering policies based on user groups or network segments. This flexibility ensures a more personalized and efficient web filtering experience.
- Reporting and Analytics: Palo Alto Networks URL Filtering provides reporting and logging capabilities, offering insights into web activity, blocked requests, and security events. This helps organizations monitor and analyze web usage, track policy violations, and gain visibility into potential security threats.
Cons
- Initial Configuration Complexity: Setting up and configuring Palo Alto Networks URL Filtering may require technical expertise and time, especially for larger deployments or complex network environments.
- Resource Requirements: Depending on the deployment model, the solution may require dedicated hardware or virtual machine resources, which could be a consideration for organizations with limited infrastructure.
- False Positives: Like any web filtering solution, Palo Alto Networks URL Filtering may occasionally flag legitimate websites as potentially harmful, resulting in false positives and potential user access restrictions.
- Dependency on URL Classification: The effectiveness of Palo Alto Networks URL Filtering depends on the accuracy and timely updating of the categorized website database. Inaccurate or delayed categorization may impact the filtering accuracy.
10. Smoothwall Web Filter
Smoothwall Web Filter is a software solution designed to control and manage internet access within an organization.
It acts as a web filtering tool that monitors and restricts user access to specific websites or web content based on predefined policies and rules.
The primary purpose of Smoothwall Web Filter is to enhance network security, increase productivity, and enforce acceptable use policies.
It analyzes web traffic in real-time, categorizes websites into different categories (such as social media, gaming, adult content, etc.), and applies filtering rules accordingly.
These rules can be customized based on the organization’s requirements and can be adjusted to allow or block specific websites or types of content.
By implementing Smoothwall Web Filter, organizations can prevent users from accessing inappropriate or malicious websites, control bandwidth usage, reduce distractions caused by non-work-related browsing, and protect against web-based threats like malware or phishing attacks.
Features
- Web Content Filtering: Filters web content based on policies and categories to enforce acceptable use policies and block access to inappropriate or malicious websites.
- Malware Protection: Detects and blocks known and unknown malware threats, including viruses, ransomware, and spyware, preventing them from entering the network.
- SSL Inspection: Decrypts and inspects SSL/TLS-encrypted web traffic to identify and prevent threats hidden within encrypted connections.
- Advanced Threat Protection: Utilizes advanced techniques, such as sandboxing and behavioral analysis, to detect and block sophisticated malware and zero-day threats.
- User Authentication: Validates user identities through various authentication methods, such as LDAP integration or single sign-on (SSO), ensuring secure access to web resources.
- URL Filtering: Controls access to specific URLs or categories of websites, allowing organizations to enforce web browsing policies and prevent access to high-risk sites.
- Application Control: Controls access to web applications, allowing organizations to define policies and restrict or block specific applications based on their requirements.
- Bandwidth Management: Manages and optimizes network bandwidth usage by controlling and prioritizing web traffic, ensuring optimal performance for critical applications.
- Reporting and Analytics: Provide detailed reports and analytics on web usage, user activities, and security events for compliance monitoring and better visibility.
- Mobile and Remote Filtering: Extends web filtering and security policies to mobile and remote users, ensuring consistent protection across different environments.
- Safe Search Enforcement: Enforces safe search policies on popular search engines to prevent users from accessing explicit or inappropriate search results.
- Cloud-based Management: Offers centralized cloud-based management for easy policy configuration, monitoring, and updates across distributed environments.
Pros
- Enhanced Security: Smoothwall Web Filter helps protect organizations from web-based threats, such as malware, phishing, and malicious websites. It blocks access to known malicious sites and provides real-time web traffic analysis, allowing organizations to identify and mitigate potential risks.
- Content Control: The web filtering capabilities of Smoothwall Web Filter enable organizations to enforce acceptable use policies and control access to inappropriate or non-work-related websites. This can improve productivity, reduce distractions, and prevent employees from accessing objectionable content.
- Bandwidth Management: Smoothwall Web Filter allows organizations to prioritize business-critical applications and allocate bandwidth resources effectively by filtering and controlling web content. This helps prevent excessive bandwidth consumption due to non-essential or bandwidth-intensive activities.
- Customization and Flexibility: Smoothwall Web Filter offers customizable filtering rules and policies, allowing organizations to tailor web filtering to their specific requirements. It provides flexibility in defining different user groups, applying specific policies, and allowing/blocking access to specific websites or categories.
Cons
- Overblocking or Underblocking: Web filtering systems like Smoothwall Web Filter may occasionally incorrectly classify legitimate websites or content, leading to overclocking (blocking authorized content) or under blocking (allowing unauthorized content). This can sometimes frustrate users or hamper access to necessary resources.
- False Positives: In some cases, Smoothwall Web Filter may mistakenly identify safe websites as malicious or inappropriate, leading to false positives. This can disrupt access to legitimate content and require manual intervention or adjustments to filtering rules.
- Resource Intensive: Implementing a web filtering solution like Smoothwall Web Filter requires dedicated hardware or software resources, which may incur additional costs. Organizations must allocate sufficient resources to ensure the smooth operation and performance of the filtering system.
- Administrative Overhead: Managing and maintaining a web filtering solution requires ongoing administration and monitoring. IT administrators need to regularly update filtering rules, review logs, and address any false positives or other issues that may arise. This can add to the administrative workload.
11. iBoss Web Security
Cipafilter Web Filter is a web filtering solution designed to manage and control internet access in educational institutions and other organizations.
It is a hardware or virtual appliance that monitors and filters web traffic based on predefined policies and rules.
The main purpose of the Cipafilter Web Filter is to provide a safe and productive online environment by blocking access to inappropriate or harmful websites and content.
It uses advanced filtering technologies to analyze web traffic in real-time and categorize websites into different categories, such as social media, gaming, or adult content.
Organizations can customize the filtering rules to align with their specific requirements.
Cipafilter Web Filter offers URL filtering, content categorization, SSL inspection, bandwidth management, and reporting capabilities.
It allows administrators to create user-based policies, enforce acceptable use policies, and monitor internet activity.
The solution also protects against web-based threats like malware and phishing attacks.
Cipafilter Web Filter can be deployed as a hardware appliance within the organization’s network or as a virtual appliance in a virtualized environment.
It integrates with existing network infrastructure and authentication systems, allowing for seamless integration and user management.
Features
- Web Content Filtering: Filters web content based on policies and categories to enforce acceptable use policies and block access to inappropriate or malicious websites.
- Malware Protection: Detects and blocks known and unknown malware threats, including viruses, ransomware, and spyware, preventing them from entering the network.
- SSL/TLS Inspection: Performs SSL/TLS decryption and inspection to identify and prevent threats hidden within encrypted web traffic.
- Advanced Threat Protection: Utilizes advanced techniques, such as sandboxing and behavioral analysis, to detect and block sophisticated malware and zero-day threats.
- User Authentication: Validates user identities through various authentication methods, ensuring secure access to web resources.
- URL Filtering: Controls access to specific URLs or categories of websites, allowing organizations to enforce web browsing policies and prevent access to high-risk sites.
- Application Control: Controls access to web applications, allowing organizations to define policies and restrict or block specific applications based on their requirements.
- Bandwidth Management: Manages and optimizes network bandwidth usage by controlling and prioritizing web traffic, ensuring optimal performance for critical applications.
- Reporting and Analytics: Provide detailed reports and analytics on web usage, user activities, and security events for compliance monitoring and better visibility.
- Mobile and Remote Filtering: Extends web filtering and security policies to mobile and remote users, ensuring consistent protection across different environments.
- Data Loss Prevention (DLP): Prevents the unauthorized transmission of sensitive data through web channels, ensuring compliance with data protection regulations.
- Cloud-based Management: Offers centralized cloud-based management for easy policy configuration, monitoring, and updates across distributed environments.
Pros
- Web Filtering Capabilities: Cipafilter Web Filter offers robust web filtering capabilities, allowing organizations to control and restrict access to inappropriate or non-work-related websites. It helps maintain a productive online environment, reduces distractions, and prevents users from accessing objectionable content.
- Enhanced Security: By blocking access to malicious websites and implementing SSL inspection, Cipafilter Web Filter helps protect organizations from web-based threats like malware, phishing, and other online attacks. It provides an additional layer of security by filtering and monitoring web traffic for potential risks.
- Customizable Policies: Cipafilter Web Filter enables organizations to define and customize filtering policies based on their specific requirements. Administrators can create user-based policies, apply different filtering rules for different groups, and control access to specific websites or categories.
- Bandwidth Management: The solution offers bandwidth management features, allowing organizations to allocate network resources effectively. It helps prioritize business-critical applications, prevent bandwidth abuse, and ensure smooth network performance.
Cons
- Initial Configuration Complexity: Setting up and configuring Cipafilter Web Filter may require technical expertise and careful consideration of organizational requirements. Initial configuration and fine-tuning of filtering rules can be time-consuming and may require ongoing adjustments to achieve optimal results.
- False Positives and False Negatives: Like any web filtering solution, Cipafilter Web Filter may occasionally generate false positives (blocking legitimate content) or false negatives (allowing inappropriate content). Administrators need to review and fine-tune filtering rules to minimize such occurrences regularly.
- Scalability Challenges: Depending on the organization’s size and network infrastructure, scaling Cipafilter Web Filter to handle increasing web traffic and user load can be challenging. Ensuring that the solution can accommodate growth and maintain performance is crucial.
- Maintenance and Updates: Cipafilter Web Filter requires regular maintenance, including updating filtering databases, software patches, and system monitoring. Organizations must allocate resources for ongoing maintenance tasks to keep the solution running smoothly.
12. Fortinet FortiGate Web Filtering

Fortinet FortiGate Web Filtering is a web filtering feature offered by Fortinet’s FortiGate network security appliances.
Organizations can monitor, control, and filter internet traffic based on defined policies.
The primary purpose of Fortinet FortiGate Web Filtering is to enhance security and productivity by managing web access within the organization.
It analyzes web traffic in real-time, categorizes websites into different categories, and applies filtering rules accordingly.
FortiGate Web Filtering offers many features, including URL filtering, content categorization, malware protection, and reporting capabilities.
It allows administrators to create customized filtering policies based on user groups, time restrictions, or specific content categories.
The solution integrates with Fortinet’s security fabric, enabling seamless communication and cooperation with other security components.
This integration enhances the overall security posture by leveraging the collective intelligence and threat intelligence feeds of the Fortinet ecosystem.
Features
- Web Content Filtering: Filters web content based on policies and categories to enforce acceptable use policies and block access to inappropriate or malicious websites.
- Malware Protection: Detects and blocks known and unknown malware threats, including viruses, ransomware, and spyware, preventing them from entering the network.
- SSL Inspection: Performs SSL/TLS decryption and inspection to identify and prevent threats hidden within encrypted web traffic.
- Advanced Threat Protection: Utilizes advanced techniques, such as sandboxing and behavioral analysis, to detect and block sophisticated malware and zero-day threats.
- User Authentication: Validates user identities through various authentication methods, ensuring secure access to web resources.
- URL Filtering: Controls access to specific URLs or categories of websites, allowing organizations to enforce web browsing policies and prevent access to high-risk sites.
- Application Control: Controls access to web applications, allowing organizations to define policies and restrict or block specific applications based on their requirements.
- Bandwidth Management: Manages and optimizes network bandwidth usage by controlling and prioritizing web traffic, ensuring optimal performance for critical applications.
- Reporting and Analytics: Provide detailed reports and analytics on web usage, user activities, and security events for compliance monitoring and better visibility.
- Mobile and Remote Filtering: Extends web filtering and security policies to mobile and remote users, ensuring consistent protection across different environments.
- Data Loss Prevention (DLP): Prevents the unauthorized transmission of sensitive data through web channels, ensuring compliance with data protection regulations.
- Cloud-based Management: Offers centralized cloud-based management for easy policy configuration, monitoring, and updates across distributed environments.
Pros
- Enhanced Security: FortiGate Web Filtering helps organizations protect against web-based threats, such as malware, phishing, and malicious websites. It blocks access to known malicious sites and provides real-time web traffic analysis, enabling proactive threat prevention.
- Flexible Filtering Policies: The solution allows organizations to create customized filtering policies based on user groups, content categories, or time restrictions. This flexibility enables fine-grained control over web access, allowing organizations to enforce acceptable use policies effectively.
- Integrated Security Ecosystem: FortiGate Web Filtering seamlessly integrates with Fortinet’s security fabric, enabling coordinated threat intelligence sharing and unified management. This integration enhances overall security effectiveness and simplifies administration.
- Reporting and Monitoring Capabilities: FortiGate Web Filtering provides comprehensive reporting and monitoring capabilities, allowing administrators to gain insights into web usage, identify potential risks, and make informed decisions regarding internet access policies.
Cons
- The complexity of Configuration: Configuring and fine-tuning FortiGate Web Filtering can be complex, especially for organizations with specific requirements or complex network infrastructures. Proper planning and expertise are necessary to ensure accurate filtering and avoid false positives/negatives.
- False Positives/Negatives: Like any web filtering solution, FortiGate Web Filtering may occasionally generate false positives (blocking legitimate content) or false negatives (allowing inappropriate content). Administrators need to review and adjust filtering policies to minimize such occurrences regularly.
- Resource Intensive: Implementing FortiGate Web Filtering requires dedicated hardware resources, which may incur additional costs. Organizations should ensure their infrastructure can handle the processing requirements and scalability of the solution.
- Dependency on Fortinet Ecosystem: While integrating Fortinet’s security fabric is a strength, it also means organizations must commit to the Fortinet ecosystem for their security infrastructure. This dependency may limit flexibility or require additional investments if transitioning away from Fortinet in the future.
13. GFI WebMonitor
GFI WebMonitor is a web filtering and internet monitoring solution designed to help organizations control and secure internet usage within their networks.
It provides real-time monitoring, web filtering, and reporting capabilities to manage and enforce internet access policies.
The primary purpose of GFI WebMonitor is to enhance productivity, enforce acceptable use policies, and protect against web-based threats.
It enables organizations to monitor and analyze internet activity, block or restrict access to specific websites or content categories, and generate detailed reports on web usage.
GFI WebMonitor offers features such as URL filtering, content categorization, bandwidth management, malware protection, and SSL inspection.
It allows administrators to create custom policies, set time-based restrictions, and apply filtering rules based on user groups or individual users.
Features
- Web Content Filtering: Filters web content based on policies and categories to enforce acceptable use policies and block access to inappropriate or malicious websites.
- Malware Protection: Detects and blocks known and unknown malware threats, including viruses, ransomware, and spyware, preventing them from entering the network.
- SSL Inspection: Performs SSL/TLS decryption and inspection to identify and prevent threats hidden within encrypted web traffic.
- Advanced Threat Protection: Utilizes advanced techniques, such as sandboxing and behavioral analysis, to detect and block sophisticated malware and zero-day threats.
- User Authentication: Validates user identities through various authentication methods, ensuring secure access to web resources.
- URL Filtering: Controls access to specific URLs or categories of websites, allowing organizations to enforce web browsing policies and prevent access to high-risk sites.
- Application Control: Controls access to web applications, allowing organizations to define policies and restrict or block specific applications based on their requirements.
- Bandwidth Management: Manages and optimizes network bandwidth usage by controlling and prioritizing web traffic, ensuring optimal performance for critical applications.
- Reporting and Analytics: Provide detailed reports and analytics on web usage, user activities, and security events for compliance monitoring and better visibility.
- Mobile and Remote Filtering: Extends web filtering and security policies to mobile and remote users, ensuring consistent protection across different environments.
- Data Loss Prevention (DLP): Prevents the unauthorized transmission of sensitive data through web channels, ensuring compliance with data protection regulations.
- Cloud-based Management: Offers centralized cloud-based management for easy policy configuration, monitoring, and updates across distributed environments.
Pros
- Web Filtering Capabilities: GFI WebMonitor offers robust web filtering features, allowing organizations to control and restrict access to inappropriate or non-work-related websites. It helps enforce acceptable use policies, reduce distractions, and maintain a productive online environment.
- Web Threat Protection: The solution helps protect organizations from web-based threats, such as malware, phishing, and malicious websites. It can block access to known malicious sites and provide real-time scanning and protection against web-borne threats.
- Bandwidth Management: GFI WebMonitor includes bandwidth management capabilities, enabling organizations to optimize network performance and allocate bandwidth resources effectively. It helps prevent excessive bandwidth usage due to non-essential or bandwidth-intensive activities.
- Comprehensive Reporting: The solution provides detailed reporting on internet usage, web activity, and potential security risks. These reports offer insights into user behavior, help identify policy violations or potential threats, and support informed decision-making.
Cons
- Initial Configuration Complexity: Setting up and configuring GFI WebMonitor may require technical expertise and careful consideration of organizational requirements. Initial configuration, including defining filtering rules and policies, can be time-consuming and may require ongoing adjustments.
- False Positives and False Negatives: Like any web filtering solution, GFI WebMonitor may occasionally generate false positives (blocking legitimate content) or false negatives (allowing inappropriate content). Administrators need to review and fine-tune filtering rules to minimize such occurrences regularly.
- Resource Requirements: Implementing GFI WebMonitor may require dedicated hardware resources or virtual machines, which may involve additional costs. Organizations should ensure their infrastructure can handle the processing requirements and scalability of the solution.
- Impact on Network Performance: Depending on the organization’s size and the web traffic volume, implementing GFI WebMonitor may introduce additional latency or impact network performance. Careful monitoring and optimization are necessary to balance security and performance.
14. OpenDNS
OpenDNS is a cloud-based DNS (Domain Name System) service that provides enhanced security, control, and performance for organizations’ internet connections.
It acts as a protective layer between users and the internet by offering advanced DNS resolution and filtering capabilities.
The primary purpose of OpenDNS is to improve security and control over internet access.
It replaces the default DNS servers provided by internet service providers (ISPs) and offers additional features, such as content filtering and threat protection.
OpenDNS utilizes a global network of servers to resolve domain names into IP addresses, enabling users to access websites and online services.
However, it goes beyond traditional DNS by providing security features like blocking access to known malicious websites, detecting and blocking phishing attempts, and offering protection against malware and botnets.
Features
- DNS Security: Provides DNS-layer security to protect against advanced threats, including malware, ransomware, phishing, and botnets.
- Threat Intelligence: Utilizes global threat intelligence feeds to identify and block access to known malicious domains, IPs, and URLs.
- Web Filtering: Filters web content based on policies and categories to enforce acceptable use policies and block access to inappropriate or malicious websites.
- Secure Web Gateway: Inspects web traffic for threats and enforces security policies, even when users are off the corporate network.
- Intelligent Proxy: Utilizes intelligent proxy capabilities to inspect and filter web traffic, providing an additional layer of security.
- Malware Protection: Detects and blocks known and unknown malware threats, preventing them from entering the network.
- Secure DNS: Offers encrypted DNS queries to ensure privacy and protect against DNS-based attacks, such as DNS hijacking and DNS spoofing.
- Reporting and Analytics: Provide detailed reports and analytics on DNS requests, web usage, security events, and threat intelligence for better visibility and compliance monitoring.
- Integration with Security Ecosystem: Integrates with other security solutions to enhance overall security posture and enable centralized management and visibility.
- Mobile and Remote Protection: Extends DNS security and web filtering policies to mobile and remote users, regardless of their location.
- Policy Enforcement: Enforces granular policies based on user, device, location, or group, allowing organizations to customize their security settings.
- Cloud-based Management: Offers centralized cloud-based management for easy policy configuration, monitoring, and updates across distributed environments.
Pros
- Enhanced Security: OpenDNS offers protection against known malicious websites, phishing attempts, and malware. By blocking access to harmful sites and detecting potential threats, it helps improve the overall security posture of an organization.
- Content Filtering: OpenDNS allows organizations to enforce internet usage policies by filtering access to specific categories of websites. This feature helps prevent users from accessing inappropriate or non-work-related content, improving productivity and reducing security risks.
- Improved Performance: OpenDNS operates on a global network of servers, which can lead to faster DNS resolution times compared to traditional DNS services. This can improve internet performance and a better user experience for employees or customers.
- Easy Implementation: Configuring OpenDNS requires minimal effort and technical expertise. It can be easily implemented by updating DNS settings on network devices or using simple software clients, making it accessible to various organizations.
Cons
- False Positives/Negatives: Like any content filtering solution, OpenDNS may occasionally generate false positives (blocking legitimate content) or false negatives (allowing inappropriate content). Administrators need to review and adjust filtering settings to minimize such occurrences.
- Limited Customization: While OpenDNS provides pre-defined categories for content filtering, customization options may be limited compared to more advanced web Content filtering solutions. Organizations with specific requirements may find the predefined categories insufficient for their needs.
- Dependency on Cloud Service: As a cloud-based service, OpenDNS relies on an internet connection and the availability of OpenDNS servers. If the service experiences outages or disruptions, it can affect internet connectivity for users relying on OpenDNS for DNS resolution.
- Data Privacy: OpenDNS processes DNS traffic, which raises concerns about data privacy and security. Organizations should carefully review OpenDNS’s privacy policies and data handling practices to ensure compliance with their privacy requirements.
15. Untangle Web Filter
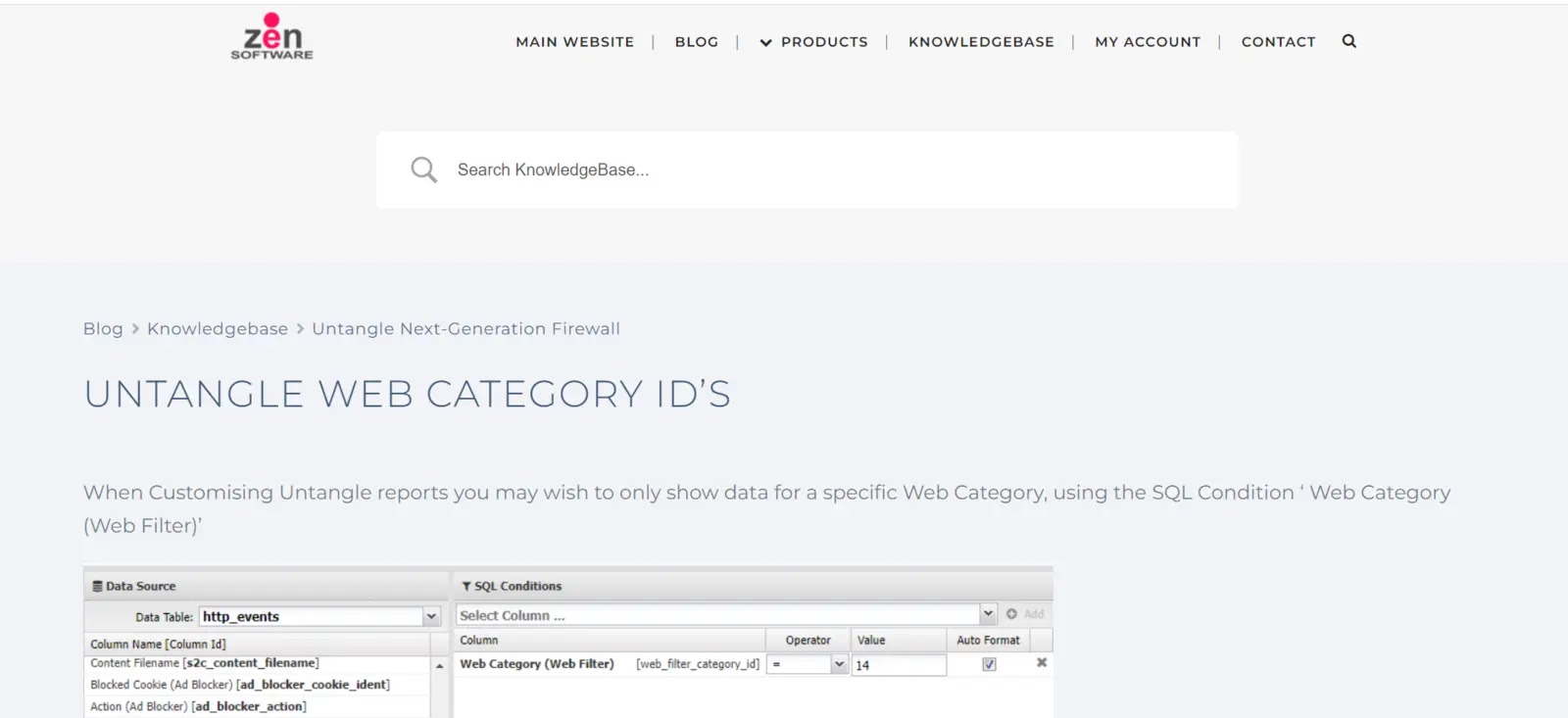
Untangle Web Filter is a comprehensive web filtering solution that allows organizations to monitor, control, and filter internet traffic.
It enables administrators to enforce acceptable use policies, block access to inappropriate or malicious websites, and protect against web-based threats.
Untangle Web Filter offers features such as URL filtering, content categorization, malware protection, and reporting capabilities to ensure a secure and productive online environment.
Features
- Content Filtering: Untangle Web Filter can block access to websites based on their content categories, such as adult content, gambling, violence, or social media. It uses URL categorization databases and advanced algorithms to analyze web page content and determine its category.
- Whitelisting and Blacklisting: It allows administrators to create custom whitelists and blacklists, giving them control over specific websites or categories that should be allowed or blocked.
- Safe Search Enforcement: Untangle Web Filter can enforce safe search settings on popular search engines, ensuring that inappropriate content is filtered out from search results.
- Bandwidth Control: It enables administrators to allocate bandwidth resources effectively by controlling and limiting access to bandwidth-intensive websites and applications. This helps prevent network congestion and ensures fair distribution of resources.
- Reporting and Logging: Untangle Web Filter provides comprehensive reporting and logging capabilities, allowing administrators to monitor web activity, track user behavior, and generate usage reports. This information can be useful for identifying potential security threats or policy violations.
- HTTPS Inspection: Some web Content filtering solutions, including Untangle Web Filter, can inspect HTTPS traffic, allowing for more effective filtering and blocking of encrypted websites.
- Malware and Phishing Protection: Untangle Web Filter may include real-time scanning of web pages for malware and phishing attempts, providing an additional layer of security to protect users from malicious content.
- Time-Based Policies: Administrators can set time-based policies to control web access during specific periods, such as blocking social media sites during work hours or restricting access to certain categories during school hours.
- User Authentication: Untangle Web Filter may integrate with existing user authentication systems, such as Active Directory or LDAP, to apply different filtering policies based on user groups or individual users.
- Remote Management: Untangle Web Filter typically offers remote management capabilities, allowing administrators to configure and monitor the filtering system from a centralized location.
Pros
- Web Filtering Capabilities: Untangle Web Filter offers robust web filtering features, allowing organizations to control and restrict access to inappropriate or non-work-related websites. It helps enforce acceptable use policies, reduce distractions, and maintain a productive online environment.
- Comprehensive Protection: The solution helps protect organizations from web-based threats, such as malware, phishing, and malicious websites. It employs advanced filtering techniques and integrates with threat intelligence feeds to detect and block potential threats.
- Customization and Granularity: Untangle Web Filter provides flexibility in creating customized filtering policies based on user groups, time restrictions, or specific content categories. Administrators can tailor the filtering rules to align with organizational requirements and fine-tune the level of control.
- Reporting and Monitoring Capabilities: Untangle Web Filter offers detailed reporting and monitoring capabilities, allowing administrators to gain insights into web usage, identify potential risks, and make informed decisions regarding internet access policies.
Cons
- Initial Configuration Complexity: Setting up and configuring Untangle Web Filter may require technical expertise and careful consideration of organizational requirements. It can involve configuring network settings, defining filtering rules, and ensuring proper integration within the existing network infrastructure.
- False Positives and False Negatives: Like any web filtering solution, Untangle Web Filter may occasionally generate false positives (blocking legitimate content) or false negatives (allowing inappropriate content). Administrators need to review and adjust filtering rules to minimize such occurrences regularly.
- Resource Requirements: Implementing Untangle Web Filter may require dedicated hardware resources or virtual machines, depending on the deployment method. Organizations should ensure their infrastructure can handle the processing requirements and scalability of the solution.
- Cost Considerations: Untangle Web Filter is a commercial solution, and depending on the organization’s size and requirements, there may be associated licensing and maintenance costs. Organizations should evaluate the cost-effectiveness and budget implications before implementing the solution.
16. WebTitan
WebTitan is a web filtering and security solution designed to protect organizations from web-based threats, enforce internet usage policies, and ensure a safe online environment.
It offers advanced filtering capabilities, content categorization, and real-time monitoring to control and secure internet access within the organization.
WebTitan helps block malicious websites, filter inappropriate content, and provide reporting and analytics on web usage.
It is a comprehensive tool that enables organizations to enhance security, increase productivity, and enforce acceptable use policies effectively.
Features
- Web Content Filtering: Filters web content based on policies and categories to enforce acceptable use policies and block access to inappropriate or malicious websites.
- Malware Protection: Detects and blocks known and unknown malware threats, including viruses, ransomware, and spyware, preventing them from entering the network.
- SSL/TLS Inspection: Performs SSL/TLS decryption and inspection to identify and prevent threats hidden within encrypted web traffic.
- Advanced Threat Protection: Utilizes advanced techniques, such as sandboxing and behavioral analysis, to detect and block sophisticated malware and zero-day threats.
- User Authentication: Validates user identities through various authentication methods, ensuring secure access to web resources.
- URL Filtering: Controls access to specific URLs or categories of websites, allowing organizations to enforce web browsing policies and prevent access to high-risk sites.
- Application Control: Controls access to web applications, allowing organizations to define policies and restrict or block specific applications based on their requirements.
- Bandwidth Management: Manages and optimizes network bandwidth usage by controlling and prioritizing web traffic, ensuring optimal performance for critical applications.
- Reporting and Analytics: Provides detailed reports and analytics on web usage, user activities, and security events for compliance monitoring and better visibility.
- Mobile and Remote Filtering: Extends web filtering and security policies to mobile and remote users, ensuring consistent protection across different environments.
- Safe Search Enforcement: Enforces safe search policies on popular search engines to prevent users from accessing explicit or inappropriate search results.
- Cloud-based Management: Offers centralized cloud-based management for easy policy configuration, monitoring, and updates across distributed environments.
Pros
- Web Filtering Capabilities: WebTitan offers robust web filtering features, allowing organizations to control and restrict access to inappropriate or non-work-related websites. It helps enforce acceptable use policies, reduce distractions, and maintain a productive online environment.
- Threat Protection: WebTitan includes advanced threat protection measures to guard against web-based threats such as malware, phishing attempts, and malicious websites. It can block access to known malicious sites and provide real-time scanning and protection against web-borne threats.
- Customization and Granularity: WebTitan allows for customizing filtering policies based on user groups, time restrictions, or specific content categories. This enables organizations to tailor filtering rules to align with their specific needs and level of control.
- Reporting and Analytics: WebTitan provides comprehensive reporting and analytics capabilities, allowing administrators to gain insights into web usage patterns, identify potential risks or policy violations, and make informed decisions regarding internet access policies.
Cons
- Initial Configuration Complexity: Setting up and configuring WebTitan may require technical expertise and careful consideration of organizational requirements. Initial configuration, including defining filtering rules and policies, can be time-consuming and may require ongoing adjustments.
- False Positives and False Negatives: Like any web filtering solution, WebTitan may occasionally generate false positives (blocking legitimate content) or false negatives (allowing inappropriate content). Administrators need to review and fine-tune filtering rules to minimize such occurrences regularly.
- Resource Requirements: Implementing WebTitan may require dedicated hardware resources or virtual machines, depending on the deployment method chosen. Organizations should ensure their infrastructure can handle the processing requirements and scalability of the solution.
- Cost Considerations: WebTitan is a commercial solution, and depending on the organization’s size and requirements, there may be associated licensing and maintenance costs. Organizations should evaluate the cost-effectiveness and budget implications before implementing the solution.
17. DNSFilter
DNSFilter is a cloud-based DNS filtering and security solution that gives organizations enhanced control over internet access and protection against web-based threats.
It filters DNS requests, allowing or blocking access to specific websites or categories based on predefined policies.
DNSFilter helps organizations enforce internet usage policies, prevent access to malicious or inappropriate content, and improve network security.
Its cloud-based architecture enables easy implementation, scalability, and real-time updates to ensure effective web filtering and threat protection.
Features
- Malware and Phishing Protection: The platform includes built-in protection against malware and phishing attacks. It identifies and blocks connections to known malicious domains and prevents users from accessing sites involved in phishing attempts, reducing the risk of data breaches and malware infections.
- Advanced Threat Intelligence: DNSFilter leverages a continuously updated threat intelligence database to stay ahead of emerging threats. It employs machine learning algorithms and behavior-based analysis to detect and block zero-day attacks and other advanced threats in real-time.
- Reporting and Analytics: DNSFilter provides comprehensive reporting and analytics to gain insights into your network’s DNS activity. You can track browsing activity, identify security threats, and generate detailed reports to monitor user behavior, identify potential risks, and ensure compliance with acceptable use policies.
- Roaming Protection: DNSFilter offers roaming protection to secure devices outside of your organization’s network. It can protect laptops, mobile devices, and remote workers by filtering DNS requests regardless of their location, ensuring consistent security across all devices.
- Granular Policy Control: The platform allows you to define granular policies and apply them to different user groups or devices. You can create policies based on IP addresses, Active Directory integration, or use API integrations to integrate with other security solutions.
- Integration and API Support: DNSFilter supports integration with other security tools and platforms through its API. It allows you to automate workflows, integrate with SIEM (Security Information and Event Management) systems, and easily incorporate DNSFilter’s functionality into your existing security infrastructure.
- Scalability and Reliability: DNSFilter operates as a cloud-based service, providing scalability and reliability to handle large volumes of DNS traffic. It uses a global network of servers distributed across multiple data centers to ensure fast and reliable DNS resolution.
- Easy Deployment and Management: DNSFilter is designed for easy deployment and management. It can be implemented without requiring any hardware installation or complex configurations. The platform offers a user-friendly interface, allowing administrators to manage policies, view reports, and make changes easily.
Pros
- Enhanced Security: DNSFilter helps protect organizations from web-based threats, such as malware, ransomware, and phishing attempts. Blocking access to malicious or compromised websites reduces the risk of users inadvertently downloading or accessing harmful content.
- Web Filtering Capabilities: DNSFilter offers powerful web filtering capabilities, allowing organizations to control and restrict access to specific websites or categories. This helps enforce acceptable use policies, improve productivity, and maintain a safe browsing environment.
- Cloud-Based Infrastructure: Being cloud-based, DNSFilter provides easy implementation and scalability. It does not require complex hardware installations or maintenance, and updates are applied automatically, ensuring that organizations have up-to-date protection without the need for manual intervention.
- Reporting and Analytics: DNSFilter provides detailed reporting and analytics on web activity, allowing administrators to gain insights into user behavior, identify potential risks, and make informed decisions regarding internet usage policies.
Cons
- Dependency on DNS: DNSFilter’s effectiveness depends on DNS requests being routed through its service. If devices bypass DNSFilter or use alternative DNS settings, the filtering and security features may be bypassed.
- False Positives/Negatives: Like any web filtering solution, DNSFilter may occasionally generate false positives (blocking legitimate content) or false negatives (allowing inappropriate content). Administrators need to review and fine-tune filtering rules to minimize such occurrences regularly.
- Lack of Granularity: DNSFilter’s filtering capabilities are primarily based on DNS requests, which may lack the granular control of more advanced web filtering solutions. Organizations with specific requirements for content categorization or customized policies may find DNSFilter’s options limited.
- Cost Considerations: DNSFilter is a commercial solution, and organizations need to evaluate the cost-effectiveness and budget implications of implementing the service, particularly for large-scale deployments.
18. McAfee Web Protection

McAfee Web Protection is a comprehensive web security solution designed to safeguard organizations from web-based threats, enforce acceptable internet usage policies, and provide advanced content filtering capabilities.
It offers features such as web filtering, malware protection, data loss prevention, and granular policy controls.
McAfee Web Protection helps organizations mitigate risks, prevent data breaches, and ensure a safe and productive online environment.
Features
- Application Control: It enables administrators to control and manage access to specific web applications and protocols. This includes blocking or allowing access to popular applications such as instant messaging, peer-to-peer file sharing, or streaming media.
- Malware Protection: McAfee Web Protection Filter includes real-time scanning of web content for malware and other malicious code. It helps prevent users from accessing websites that contain malware, viruses, or other forms of malicious content.
- Data Loss Prevention (DLP): It offers DLP capabilities to detect and prevent the unauthorized transmission of sensitive or confidential data. Administrators can define policies to monitor and block the transfer of sensitive information over web-based channels.
- SSL/TLS Inspection: McAfee Web Protection Filter can inspect encrypted HTTPS traffic, allowing for more effective filtering and blocking of encrypted websites. It helps prevent malicious activities that might be concealed within encrypted connections.
- Web Application Firewall (WAF): Some versions of McAfee Web Protection Filter include a WAF component, which provides protection against web application attacks, such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
- Advanced Threat Protection: McAfee Web Protection Filter may incorporate advanced threat detection technologies, such as sandboxing or machine learning, to identify and block sophisticated threats like zero-day exploits and targeted attacks.
- Reporting and Analytics: It provides comprehensive reporting and analytics capabilities, allowing administrators to monitor web activity, track user behavior, and generate detailed reports on usage, threats, and policy violations.
- User Authentication: McAfee Web Protection Filter can integrate with existing user authentication systems, such as Active Directory or LDAP, to apply different filtering policies based on user groups or individual users.
- Centralized Management: McAfee Web Protection Filter offers centralized management capabilities, allowing administrators to configure, monitor, and control the filtering solution from a central console.
Pros
- Web Security: McAfee Web Protection offers robust protection against web-based threats, including malware, phishing attempts, and malicious websites. It helps prevent users from accessing harmful content and reduces the risk of security breaches.
- Web Filtering Capabilities: The solution provides powerful web filtering features, allowing organizations to enforce internet usage policies and restrict access to inappropriate or non-work-related websites. It helps improve productivity, reduce distractions, and maintain a secure browsing environment.
- Data Loss Prevention: McAfee Web Protection includes data loss prevention (DLP) capabilities, which help prevent sensitive data from being leaked or shared inappropriately. It can detect and block attempts to transmit confidential information through web channels.
- Centralized Management: McAfee Web Protection offers centralized management, allowing administrators to configure and control web security policies across the organization. It provides a unified console for monitoring and managing web security settings, simplifying administration and enhancing efficiency.
Cons
- The complexity of Configuration: Setting up and configuring McAfee Web Protection may require technical expertise and careful consideration of organizational requirements. Initial configuration and policy fine-tuning may involve a learning curve for administrators.
- False Positives/Negatives: Like any web filtering solution, McAfee Web Protection may generate false positives (blocking legitimate content) or false negatives (allowing inappropriate content) in certain situations. Regular monitoring and adjustment of filtering rules are necessary to minimize these occurrences.
- Resource Requirements: Implementing McAfee Web Protection may require dedicated hardware resources or virtual machines, depending on the deployment method chosen. Organizations should ensure their infrastructure can handle the processing demands and scalability of the solution.
- Cost Considerations: McAfee Web Protection is a commercial solution, and organizations need to evaluate the associated licensing and maintenance costs based on their size and requirements. It is important to assess the cost-effectiveness and budget implications before implementing the solution.
Conclusion
Several effective web filtering solutions are available in the market to meet organizations’ security and productivity needs.
The best web filtering solution will depend on each organization’s specific requirements, budget, and preferences.
Solutions such as Untangle Web Filter, DNSFilter, and McAfee Web Protection offer robust web filtering capabilities, advanced threat protection, and customizable policies.
When selecting a web filtering solution, organizations should consider factors such as the level of security provided, ease of implementation and management, scalability, reporting, analytics capabilities, and cost considerations.
It is crucial to evaluate the pros and cons of each solution in relation to the organization’s unique requirements.
Regardless of the chosen solution, implementing a web filtering solution can help organizations enforce acceptable internet usage policies, protect against web-based threats, and improve productivity by filtering out inappropriate or non-work-related content.
Regular monitoring, policy fine-tuning, and staying updated with emerging threats are essential to ensure the ongoing effectiveness of the chosen web filtering solution.
Go to Source
Author: Cyber Writes Team








