Security Incident Response
Incident response Tools or incident management software are essential security solutions to protect businesses and enterprises from cyber attacks.
Our reliance on the internet is growing, and so make a threat to businesses, despite increased investments and expertise in internet security. More data breaches and cyberattacks exist on organizations, governments, and individuals than ever before.
New technologies like Machine Learning, Artificial Intelligence, and 5G, as well as better coordination between hacker groups and state actors, have made threats riskier.
The faster your organization detects and responds to an unauthorized access or IoT security incident, the less likely it is to have a negative impact on the information, customer trust, reputation, and profitability.
What is an Incident Response?
Incident response refers to an organization’s strategy for responding to and managing a cyberattack. A cyberattack or security violation may lead to chaos, copyright claims, a drain on overall organizational resources and time, and a decline in brand value.
An incident response aims to mitigate damage and speedily return to normalcy. A well-defined incident response plan can restrict attack damage and save money and time after a cyber attack.
Why Incident Response Tools are Important?
Incident response manages the repercussions of an IoT security breach or failure.
Before an incident occurs, it is critical to have a response procedure in place to limit the extent of damage caused by the event and save the organization time and money in the recovery process.
There are several best incident response tools often used by organizations to detect and mitigate cyberattacks.
Here we have listed some of the most important cyber incident response software that are widely used with the most sophisticated features.
As you know investigation is always required to safeguard your future you must learn about the attack and be prepared for it.
Security Incident Response software have to be available for every organization to identify and address exploits, malware, cyberattacks, and other external security threats.
These Incident Response Tools usually work with other traditional security solutions like firewalls and antivirus, to analyze the attacks before it happens.
For doing this appropriately, these tools gather the information from the logs, identity system, endpoints, etc. it also notices suspicious activities in the system.
If we use these best Incident Response Tools it becomes easy for us to quickly monitor, resolve, and identify security issues.
It streamlines the process and eliminates repetitive tasks manually.
Maximum modern tools have multiple capacities where they can block, and detect the threat and they can even alert the security teams to investigate further issues.
Security terms differ for different areas, and it completely depends on the organization’s needs. In this case, pleases select the best tool is always challenging, and it also has to give you the right solution.
What’s in the Incident Response Tools Article?
- Introduction
- Why Incident Response software are Important?
- What is an Incident Response?
- Incident Response Phases
- What is an Incident Response Tool?
- Why do we use Incident Response Tool?
- Table of Contents
- Incident Response Tools Features
- Demo Video
- Pros & Cos
- IR Tool Users
- Price for each Tool
- Conclusion
Incident Response Phases
The incident response methods are based on six important steps: preparation, identification, containment, eradication, recovery, and lesson.
| Incident Response Phases | How to Respond |
| Preparation | This will require figuring out the exact members of the response team and the stimulates for internal partner alerts. |
| Identification | This is the process of finding threats and responding effectively and quickly. |
| Containment | After figuring out what to do, the third step is to limit the damage and stop it from spreading. |
| Eradication | This step entails eliminating the threat and restoring internal systems as precisely as possible to their initial state. |
| Recovery | Security experts must make sure that all of the compromised systems are no longer risky and can be put back online. |
| Lesson | One of the most important and often forgotten steps. The incident response team and its partners get together to talk about how to improve their work in the future. |
In today’s technology-driven society, organizations face increasing security risks that have become unavoidable.
Therefore, the incident response team needs robust incident response tools to overcome and manage security incidents.
So let’s first understand what is an incident response tool and, after that, dive deep into the tools.
Why do we use Incident Response Tool?
Even though businesses have a lot of security practices in place, the human factor is still the most important.
According to the annual Verizon Data Breach Investigations Report, over 85% of all breaches are caused by phishing attacks.
IT security professionals need to be ready for the worst since 13% of breaches caused by people contain ransomware, and 10% of ransomware attacks cost organizations an average of $1 million. For this reason, organizations should invest in incident response software.
The incident response tools are crucial because they help businesses detect and respond to cyberattacks, manipulates, malware, and other security threats both inside and outside the organization in a reasonable timeframe.
The majority of today’s incident response software have several features, including the ability to automatically detect and block threats while notifying the appropriate security teams to look into the issue.
Depending on the organization’s needs, incident response tools may be used in various ways.
This could involve keeping an eye on the system and individual nodes, networks, assets, users, and possibly others.
Many organizations find it hard to choose the best incident response software.
To help you find the right solution, here is a list of incident response tools that can help you discover, prevent, and deal with different security threats and attacks on your IoT security tools system.
How do We Pick the Best Incident Response Tools?
We analyze the industry with the requirement to protect digital assets and discussed the respective industries’ needs with the experts based on the following Points.
How effectively are the incident response software performing for the following operations?
- Preparation & Identification
- Containment & Eradication
- Recovery and restoration
- Event False positive Checks
- Identification of incidents
- Containment and quarantine of attackers and incident activity
- Recovery from incidents, including restoration of systems
- Features, Speed, User friendly
- Activities in each phase of incident response
Incident Response Market
| By Security Type | Web Security Application Security Endpoint security Network Security Cloud Security |
| By Deployment Mode | Cloud On-premises |
| By Organization Types | Small Enterprises Medium Enterprises Large Enterprises |
Best Cyber Incident Response Tools List
| Incident Response Tools | Key Features |
|---|---|
| 1. ManageEngine | 1. It examines on-premises systems and cloud platforms 2. Logs are consolidated and stored. 3. Use User and Entity Behaviour Analytics (UEBA) to keep track of standard events. 4. The ManageEngine package has other security features like data integrity tracking and a threat intelligence 5. feed that makes threat hunting faster. |
| 2. SolarWinds | 1. User Activity Monitoring. 2. File Integrity Monitoring. 3. Network Security Monitoring. 4. Microsoft IIS Log Analysis. 5. Firewall Security Management. 6. Network Security Tools. 7. Snort IDS Log Analysis. 8. IT DISA STIG Compliance. |
| 3. CrowdStrike Falcon Insight XDR | 1. Unparalleled coverage 2. Speed investigations 3. Threat intel integration 4. 24/7 managed threat hunting 5. Continuous raw events capture 6. proactive threat hunting |
| 4. IBM QRadar | 1. Excellent filtering to produce the desired outcomes 2. Excellent threat-hunting capabilities 3. Netflow analysis 4. Capability to analyze large amounts of data quickly 5. Identify hidden threads 6. Analytics of user behavior |
| 5. Splunk | 1. Query-based historical and current analysis. 2. AI-powered threat detection. 3. It works with Windows, Linux, and macOS. |
| 6. AlienVault | 1. Compatible with Linux and Windows 2. Monitoring of behavior 3. Detection of intrusions |
| 7. LogRhythm | 1. It has a response playbook 2. Automated smart responses 3. Back-end for Elasticsearch that is open source. |
| 8. Varonis | 1. Investigating potential incidents 2. Containment, eradication, and recovery 3. Advice on detections, procedures, and cyber resilience 4. Deep forensics analysis |
| 9. OpenVAS | 1. An Advanced Task Wizard is also included in the OpenVAS web interface. 2. It includes several default scan configurations and allows users to create custom configurations. |
| 10. Rapid7 InsightlDR | 1. Endpoint Detection and Response (EDR) 2. Network Traffic Analysis (NTA) 3. User and Entity Behavior Analytics (UEBA) 4. Cloud and Integrations. 5. Security Information and Event Management (SIEM) 6. Embedded Threat Intelligence. 7. MITRE ATT&CK Alignment. 8. Deception Technology. |
| 11. Snort | 1. Modifications and extensions are feasible. 2. Customized tests and plugins are supported |
| 12. Suricata | 1. It supports JSON output 2. It supports Lua scripting 3. Support for pcap (packet capture) 4. This tool permits multiple integrations. |
| 13. Nagios | 1. It is simple to identify network issues and provide security and scalability. 2. It also helps with keeping track of logs and databases. 3. It has an easy-to-use and informative web interface that makes it easy to monitor a network. |
| 14. Sumo Logic | 1. Monitor & troubleshoot 2. Integrate real-time threat intelligence 3. Monitor & troubleshoot 4. integrated logs, metrics, and traces 5. Quickly detect applications & Incidents |
| 15. Dynatrace | 1. Full stack availability and performance monitoring 2. Easy monitoring with no configuration 3. Automated Incident Management4. 4. AWS Monitoring 5. Azure Monitoring 6. Kubernetes Monitoring |
Top 10 Best Incident Response Tools
- ManageEngine
- SolarWinds
- CrowdStrike Falcon Insight XDR
- IBM QRadar
- Splunk
- AlienVault
- LogRhythm
- Varonis
- OpenVAS
- Rapid7 InsightlDR
- Snort
- Suricata
- Nagios
- Sumo Logic
- Dynatrace
1. ManageEngine
The ManageEngine EventLog Analyzer is a Security Information and Event Management (SIEM) tool that analyses the different logs and pulls out information about performance and security.
User and Entity Behaviour Analytics (UEBA) keeps track of standard events so that a profile can be made for each user account and device.
This method is very good at finding intruders and insiders trying to steal information or take over accounts.
ManageEngine log management component collects Windows Events and Syslog messages and interacts with over 700 software applications to retrieve activity data.
The tool can also retrieve log data from AWS, Azure, and Salesforce cloud platforms.
These logs are centralized, transformed into a standard format, searched, and filed.
These saved logs are useful for PCI DSS, GDPR, FISMA, HIPAA, SOX, and GLBA compliance auditing.
This is one of the best Incident Response Tools which focuses on and analyzes the various logs and takes care of security.
It also identifies the log server and reports the unusual thing to the records.
It catches very easily unauthorized access to the IT system of the organization very easily.
There are a few target areas like web servers, databases, DHCP servers, email services, etc. which provide essential services.
This application works on Linux systems, and Windows and this has data protection standards like HIPPA, DSS, PCI, ISO 27001, etc.
| Pros | Cons |
|---|---|
| Customize tools | Self-service options and knowledge bases for customers need to be strengthened. |
| Most valuable interface | It is not simple to adjust settings while on the go, so the interface and user experience must be enhanced. |
| Very well ticketing system | Interface difficulties reported |
Users
- Security Analyst
- Incident Responder
- Security Engineer
- Threat Analyst
- SOC Analyst
- SOC Manager
- Cyber security researcher
- Independent Software Vendors
- Managed Security Service providers
- Incident Response Service Vendors
- Cyber security Vendors
Industries
- Information Technology and Services
- Computer Software
- Information security
- Government Agencies
- Financial services
- Healthcare industry
2. SolarWinds
This is another very Best Incident response tool in log management and reporting.
It gives a real-time incident response. SolarWinds analyze and identify threats quickly and allow teams to monitor and address the threat.
This tool is very simple for visualization which allows the user to identify suspicious activity.
It also has a dashboard that gives the details of every threat which helps the developers to detect the problem.
SolarWinds has an option for automating threat response; through this, you can monitor USB drives.
It also allows you to do log filtering and has node management options.
This is best for all types of business and works with Linux and Windows.
| Pros | Cons |
|---|---|
| Easy to Configure | New SEM Tool |
| Active and quick Response | Pre-learning required to use the tool |
| Simple and affordable licensing | Slow loading process identified |
Users
Industries
- Information Technology and Services
- Computer Software
- Information security
- Government Agencies
- Financial services
- Healthcare industry
Industries
- Information Technology and Services
- Computer Software
- Information security
- Government Agencies
- Financial services
- Healthcare industry
3. CrowdStrike Falcon Insight XDR
Falcon Insight XDR is a CrowdStrike-owned incident detection and response platform for enterprise networks and severing across the globe.
It provides deep threat visibility to speed up security operations to protect against cyber attacks.
CrowdStrike performs the detection and response with extended capabilities to unlock cross-domain detections and investigations across the entire enterprise.
The Falcon Incident response tool connects all the devices accessing the network and provides a single point of analysis by Creating a cohesive, more effective cybersecurity ecosystem.
The IR software offers Deep, native telemetry and also provides third-party integrations across key security domains.
Falcon Insight XDRVideo Demo:
Users
- Security Analyst
- Incident Responder
- Security Engineer
- Threat Analyst
- SOC Analyst
- SOC Manager
- Cyber security researcher
- Managed Security Service providers
- Incident Response Service Vendors
- Cyber security Vendors
Industries
- Information Technology and Services
- Computer Software
- Information security
- Government Agencies
- Financial services
- Healthcare industry
4. IBM QRadar
IBM QRadar Security Information and Event Management (SIEM) is an excellent incident response tool that helps security teams learn about threats and arrange them in order of priority.
Qradar collects information about assets, users, networks, clouds, and endpoints and then compares it to data about threats and vulnerabilities.
After that, it uses sophisticated analytics to identify and follow the spread of threats across systems.
The solution generates insightful information about the vulnerabilities that have been found.
This reveals the origin and breadth of security problems, empowering response and remediation teams to quell the threats’ spread and mitigate their effects swiftly.
It is one of the widely used Incident Response software that understands the threats and prioritized all responses.
Any data first correlates against the threat then it shows its intelligence and vulnerability.
It also tracks the threat, and they do penetrate and propagate the threat through the system.
This application creates intelligent insight that helps to detect security issues.
It allows for finding the root cause, which helps to eliminate the threats and stop spreading quickly.
This complete solution can diversify the features including risk and security to stimulate potential attackers.
This is best for medium and large-scale businesses, and it can deploy all the hardware, software, cloud, and SaaS environment.
It quickly analyzes the threat of bulk data.
The IBM QRadar tools
IBM QRadar contains a variety of data processing aiding tools. The essential ones are:
- IBM QRadar Vulnerability Manager
- IBM QRadar Risk Manager
- IBM QRadar Incident Forensics
| Pros | Cons |
|---|---|
| QRadar gives you a full view of what’s going on. It helps get a unified view of the data transfers, activities, and logs in SaaS (software-as-a-service), IaaS (infrastructure-as-a-service), and on-premises environments. | When QRadar finds something, it makes something it calls an “off ense.” So, it has a simple system for selling tickets. |
| It actively looks for security vulnerabilities in Network devices and applications. | You just have to pay close attention to how many events happen per second because that’s where the cost becomes a big issue. |
Users
- Security Analyst
- Incident Responder
- Security Engineer
- Threat Analyst
- SOC Analyst
- SOC Manager
- Cyber security reseracher
- Incdipendent Software Vendors
- Managed Security Service providers
- Incident Response Service Vendors
- Cyber security Vendors
Industries
- Information Technology and Services
- Computer Software
- Information security
- Government Agencies
- Financial services
- Healthcare industry
5. Splunk
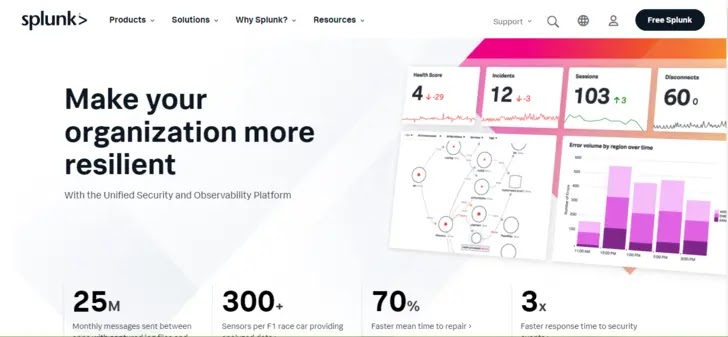
Splunk is an all-encompassing incident response tool designed for extensive network management.
Splunk’s incident response is centered on AI-powered security monitoring and prevention.
This system continuously monitors suspicious activity, threats, and policy violations.
Splunk’s security services, which actively look through log data and keep an eye on the network in real time, are powered by AI and machine learning to a large extent.
Events are looked at, grouped, and then given a threat score that tells you how bad a situation could be.
LogRhythm can read between the lines and spot attacks based on their behavior patterns, not just their payload signatures, which other signature-based tools can’t do.
This is mainly used for machine learning and AI technology which are actionable, predictive, and effective.
It also enhanced the security features and customized the statical analysis, investigation, incident review, classification, dashboard, etc.
For doing the SaaS deployment, it is suitable for all types of businesses, including small and large.
Due to its scalability, it includes other assistance like healthcare, financial service, and the public sector.
Splunk can quickly establish the risk score, good in alert management, and provides a fast and effective response.
Demo Video
| Pros | Cons |
|---|---|
| It contains numerous extensions and plugins | The cost of data is typically higher for larger volumes of data. |
| It features a magnificent dashboard with charting and search tools. | Continuously attempting to replace it with open alternative software |
| It generates analytical reports employing visual graphs and communal tables and charts. |
Users
- Security Analyst
- Incident Responder
- Security Engineer
- Threat Analyst
- SOC Analyst
- SOC Manager
- Cyber security researcher
- Independent Software Vendors
- Managed Security Service providers
- Incident Response Service Vendors
- Cyber security Vendors
Industries
- Information Technology and Services
- Computer Software
- Information security
- Government Agencies
- Financial services
- Healthcare industry
6. AlienVault
AlienVault is one of the very comprehensive Incident Response Tools for threat detection.
AlientVault is also best for compliance management so that it can provide the best security monitoring. It can do all types of remediation for the cloud environment.
It also includes multiple security capabilities like detection, asset discovery, vulnerability assessment, inventory, event correlation, compliance checks, email alerts, etc.
AlientVault is affordable in cost which is very easy to implement and it uses the USM tool which relies on lightweight sensors.
This works like an endpoint agent which can detect the threat in real-time.
It has a flexible plan for any organization to see the threat. A single web portal is enough to monitor everything.
AlienVault is a comprehensive security solution for organizations of any size, offering real-time threat detection, incident response, and compliance management.
Distributed sensors and endpoints in your network collect both log data and factual information.
AlienVault is now part of AT&T Cybersecurity, which offers various additional security services and tools that organizations may wish to investigate.
| Pros | Cons |
|---|---|
| It has a unified security platform | If the systems used by cross-border partners are unreliable, it can be quite simple to launch attacks against their databases. |
| Unlimited threat intelligence | This can compromise the system’s ability to recognize threats. |
| Multiple deployment options |
Users
- Security Analyst
- Incident Responder
- Security Engineer
- Threat Analyst
- SOC Analyst
- SOC Manager
- Cyber security reseracher
- Incdipendent Software Vendors
- Managed Security Service providers
- Incident Response Service Vendors
- Cyber security Vendors
Industries
- Information Technology and Services
- Computer Software
- Information security
- Government Agencies
7. LogRhythm
This accommodates all types of superior features which does the log correlation with artificial intelligence.
It even works for behavioral analysis by using artificial intelligence and analyzing the traffic. LogRhythm works with platforms like Windows and Linux systems.
Its data storage is very flexible, and it is also suitable for fragmented workflow.
It also provides the extra addition for threat detection, though the data is not structured.
This does not have adequately structured data, no good visibility or automation, etc.
This is best for small and big businesses and it works with windows and other network sites.
This is compatible with different logs and devices.
LogRhythm incident response tool combines search analytics and machine learning to help you respond quickly to security incidents and get security additional insight that you can use to improve the network.
The platform’s back end is Elasticsearch, which can be hard to learn for people who have never used the open-source search tool before.
The search engine looks through the logs for trends, signs of risks, causal links, and behavioral changes to find threats and stop them before they can do harm.
Using firewall rules, automated actions can be set up, and advanced persistent threats can send real-time alerts to the security staff.
| Pros | Cons |
|---|---|
| Log ingestion | Multiple equipment with distinct entry points |
| Using the AI engine’s regulations, it quickly detects confrontational activity. | Executing extensive web searches during web traffic can make it somewhat unstable. |
Users
- Security Analyst
- Incident Responder
- Security Engineer
- Threat Analyst
- SOC Analyst
- SOC Manager
- Indipendent Software Vendors
- Managed Security Service providers
- Incident Response Service Vendors
- Cyber security Vendors
Industries
- Information Technology and Services
- Computer Software
- Information security
- Government Agencies
- Financial services
- Healthcare industry
8. Varonis
This is a very handy tool that mainly uses for infrastructure, data access, usage, users, etc. Varonis also provides alerts, actionable reports, customization, flexibility, and other suspicious activity.
It also gives a comprehensive dashboard where users can analyze the security terms which add visibility in their data and system.
It is an excellent tool for an email security system where unstructured data is available and it gives the best response for resolving issues.
It can immediately block the user who attempts access without permission or used an unauthorized IP address for login to the organization network.
This varnish is an incident response tool that provides enhanced insight and alerts before any attack. It provides LogRhythm and enhances threat detection; it never fails from the responsibility and responds correctly.
It streamlines the operation, which very quickly investigates the threats for the users.
The varonis incident response tool is used with the SIEM tools to add more context, reduce notify lethargy, and get the most useful insights.
varonis DatAlert uses data to find threats, which complements the network-focused approach of SIEM and adds more context through its powerful User Entity Behavior Analytics (UEBA) features.
By identifying overprivileged users and providing advanced remediation features, varonis DatAdvantage helps organizations concerned with compliance to reduce overall business risk.
To help the organization feel secure with its data security strategy, varonis integrates with SIEM applications to provide security analytics with rich data context.
The additional source of information that varonis provides gives security teams useful analysis and alerts about the infrastructure without adding extra work or frequency noise to the SIEM.
By using SIEM with varonis, SOC teams look into things faster and learn more about the most key resources they need to protect: detailed information and email.
| Pros | Cons |
|---|---|
| DSPM | Complex Intergaration |
| Data discovery & classification | Month plan price is high |
| Insider Risk Management Software |
Users
- Security Analyst
- Incident Responder
- Security Engineer
- Threat Analyst
- SOC Analyst
- SOC Manager
- Managed Security Service providers
- Incident Response Service Vendors
- Cyber security Vendors
Industries
- Information Technology and Services
- Computer Software
- Information security
- Government Agencies
- Financial services
- Healthcare industry
Advantage
- With the help of Varonis alerts and dashboards, investigations can be conducted more quickly and efficiently.
- Send a message to targeted search results
- Important information is displayed at a peek, along with actionable insights and a lot of background.
9. OpenVAS
Greenbone Networks maintains and distributes the Open Vulnerability Assessment System (OpenVAS), which is a vulnerability scanner.
It is designed to be an all-in-one vulnerability scanner, with various built-in tests and a Web interface that makes setting up and conducting vulnerability scans quick and easy while also offering a high level of user customization.
To scan for security vulnerabilities, employ OpenVAS, which is compatible with Linux.
It comes with its own virtual machine or can be set up from the ground up using the code that is available under the GNU’s General Public License (GPL).
| Pros | Cons |
|---|---|
| It is free and open source and can perform more advanced functions than other tools, such as Nessus. | It is difficult to install, configure, and use |
Users
- Security Analyst
- Incident Responder
- Threat Analyst
- SOC Analyst
- SOC Manager
- Cyber security reseracher
- Incdipendent Software Vendors
- Managed Security Service providers
- Incident Response Service Vendors
Industries
- Information Technology and Services
- Computer Software
- Information security
- Government Agencies
- Financial services
- Healthcare industry
10. Rapid7 InsightlDR
This SIEM tool does the data collection, search, analysis features, phishing, malware, etc.
It detects quickly any suspicious activities for both internal and external users.
This has advanced deception technology that detects the user’s behavioral analytics.
It also has other discovery features like file integrity monitoring, log management, and much more.
This is a suitable tool for any scan where they do real-time detection of all types of security threats for small, large, and medium-sized businesses.
It provides the proper search at the end and helps to make a quick and smart decision.
| Pros | Cons |
|---|---|
| Endpoint Detection and Response (EDR) | Subscription data is less |
| Cloud and Integrations | Year plan is more costly than other vendors |
| MITRE ATT&CK Alignment | Prices differ for local and international |
Users
- Security Analyst
- Incident Responder
- SOC Analyst
- SOC Manager
- Independent Software Vendors
- Managed Security Service providers
- Incident Response Service Vendors
Industries
- Information Technology and Services
- Computer Software
- Information security
- Government Agencies
- Financial services
- Healthcare industry
Price
You can get a free trial and personalized demo from here.
11. Snort

CISCO provides an open-source intrusion prevention system called Snort.
It detects intrusions and prevents attacks by taking action based on traffic patterns; it can function as an intrusion prevention system (IPS). On IP/TCP address, Snort performs protocol analysis and packet logging.
It also functions as a packet sniffer similar to tcpdump, a packet logger, a network file logging device, and a real-time network prevention system.
| Pros | Cons |
|---|---|
| It is quick and easy to install on networks. | The administrator must come up with their own ways to log and report. |
| Rules are easy to write. | Token ring is not supported in Snort |
| It has good support available on Snort sites and its own listserv. | Despite its adaptability, commercial intrusion detection systems have features that Snort does not have. |
| It is free for administrators who need a cost-effective IDS. |
Users
- Security Analyst
- Incident Responder
- Security Engineer
- Threat Analyst
- SOC Analyst
- SOC Manager
- Cyber security researcher
- Independent Software Vendors
- Managed Security Service providers
- Incident Response Service Vendors
- Cyber security Vendors
Industries
- Information Technology and Services
- Computer Software
- Information security
- Government Agencies
- Financial services
- Healthcare industry
Price
You can get a free trial and personalized demo from here.
12. Suricata

The Open Information Security Foundation (OSIF) developed the Suricata incident response tool.
It is a free tool that is used by businesses of all sizes. It is an open-source detection engine that works as both an intrusion detection system (IDS) and an intrusion prevention system (IPS) (IPS).
The system detects and prevents threats using a set of rules and a language for signatures.
Suricata is compatible with Windows, Mac OS, Unix, and Linux.
| Pros | Cons |
|---|---|
| It is lightweight and low cost | The interface is a little complex |
| It is multi-threaded, allowing for greater load balancing | Less frequent futures update |
Users
- Security Analyst
- Incident Responder
- Security Engineer
- Threat Analyst
- SOC Analyst
- SOC Manager
- Cyber security researcher
- Security Researcher
- Managed Security Service providers
- Incident Response Service Vendors
- Cyber security Vendors
Industries
- Information Technology and Services
- Computer Software
- Information security
- Government Agencies
- Financial services
- Healthcare industry
13. Nagios
Nagios is a powerful monitoring incident response tool that helps organizations to detect and resolve IT infrastructure issues before they disrupt information assets.
Designed with scalability and adaptability in mind, Nagios provides the assurance that the organization’s operational processes will not be affected by unexpected shutdowns.
Many types of network services can be monitored, such as SMTP, HTTP, POP2, SNMP, NNTP, SSH FTP, and many more.
The host’s resources, such as processor load, system log, and disk space, can also be monitored.
It works on Microsoft Windows, Linux, and other operating systems.
| Pros | Cons |
|---|---|
| It helps to make services, servers, applications, and processes more available so that users can use them to monitor the network | The network throughput can’t be tracked, and bandwidth and availability problems can’t be tracked either. |
| It makes it easy to find protocol failures, network outages, and server outages so that they can be fixed. | In the free version, there are limited features. |
| It is not possible to manage a network. |
Users
- Security Analyst
- Incident Responder
- Security Engineer
- MSP Providers
- Threat Analyst
- SOC Analyst
- SOC Manager
- Cyber security researcher
- Managed Security Service providers
- Cyber security Vendors
Industries
- Information Technology and Services
- Computer Software
- Information security
- Government Agencies
- Financial services
- Healthcare industry
14. Sumo Logic
This is a cloud-based intelligent security platform, that does the best analysis and works with SIEM solutions. This is a multi-cloud platform that also provides a hybrid environment.
This platform gives you a machine-learning experience to enhance threat detection.
It also investigates and solves security issues in real-time. It is completely based on a unified data model, which allows the security teams to consolidate the security analytics.
For using this, it does not need any costly hardware or upgraded software.
It provides real-time security visibility to the organization so that it can quickly identify isolated threats.
This configures the security system and monitors the infrastructure, applications, etc.
| Pros | Cons |
|---|---|
| Cloud-native SaaS analytics | To many options make complex Integration |
| Best Infrastructure Monitoring | Pricing |
| Hundreds of native integrations |
Users
- Security Analyst
- Incident Responder
- Security Engineer
- SOC Analyst
- SOC Manager
- Cyber security researcher
- Managed Security Service providers
- Incident Response Service Vendors
- Cyber security Vendors
Industries
- Information Technology and Services
- Computer Software
- Information security
- Government Agencies
- Financial services
- Healthcare industry
15. Dynatrace
This is one of the best Incident response Software which can simplify cloud complexity.
It also does accelerate digital transformation and gives the automatic observability scale.
If we talk about Dynatrace, it has a huge underlying infrastructure where users can make faster innovations.
It can collaborate everything very efficiently with less effort.
Many large enterprises trust this software tool that is not only modernized and also automates cloud operation.
It also delivers an unrivaled digital experience.
| Pros | Cons |
|---|---|
| Continuous, automatic discover | Less interaction |
| Process-to-process relationships | The cost is little high |
| Intuitive infographics |
Users
- Security Analyst
- Incident Responder
- Cyber security Analyst
- Threat Analyst
- SOC Analyst
- SOC Manager
- Managed Security Service providers
- Incident Response Service Vendors
Industries
- Information Technology and Services
- Computer Software
- Information security
- Government Agencies
- Financial services
- Healthcare industry
Conclusion
Cyber-attacks and threats are increasing day by day, so we need to keep track of everything so that our business goes safe.
There are the above Incident Response Tools that help to monitor the logs, detect many suspicious activities, protect data, and many other things
Go to Source
Author: Cyber Security News Team









