.webp)
The WordPress Stripe Payment Gateway plugin has been vulnerable to Unauthenticated Insecure Direct Object Reference (IDOR) Vulnerability. WooCommerce developed this plugin.
The plugin version is 7.4.1 and has nearly 900K installations worldwide. Usually, payments are redirected to externally hosted checkout pages where the checkout and payment process happens.
The use of this plugin is to make customers stay on the wordpress site during the payment.
CVE-2023-34000: IDOR vulnerability in WooCommerce Stripe Payment Gateway plugin
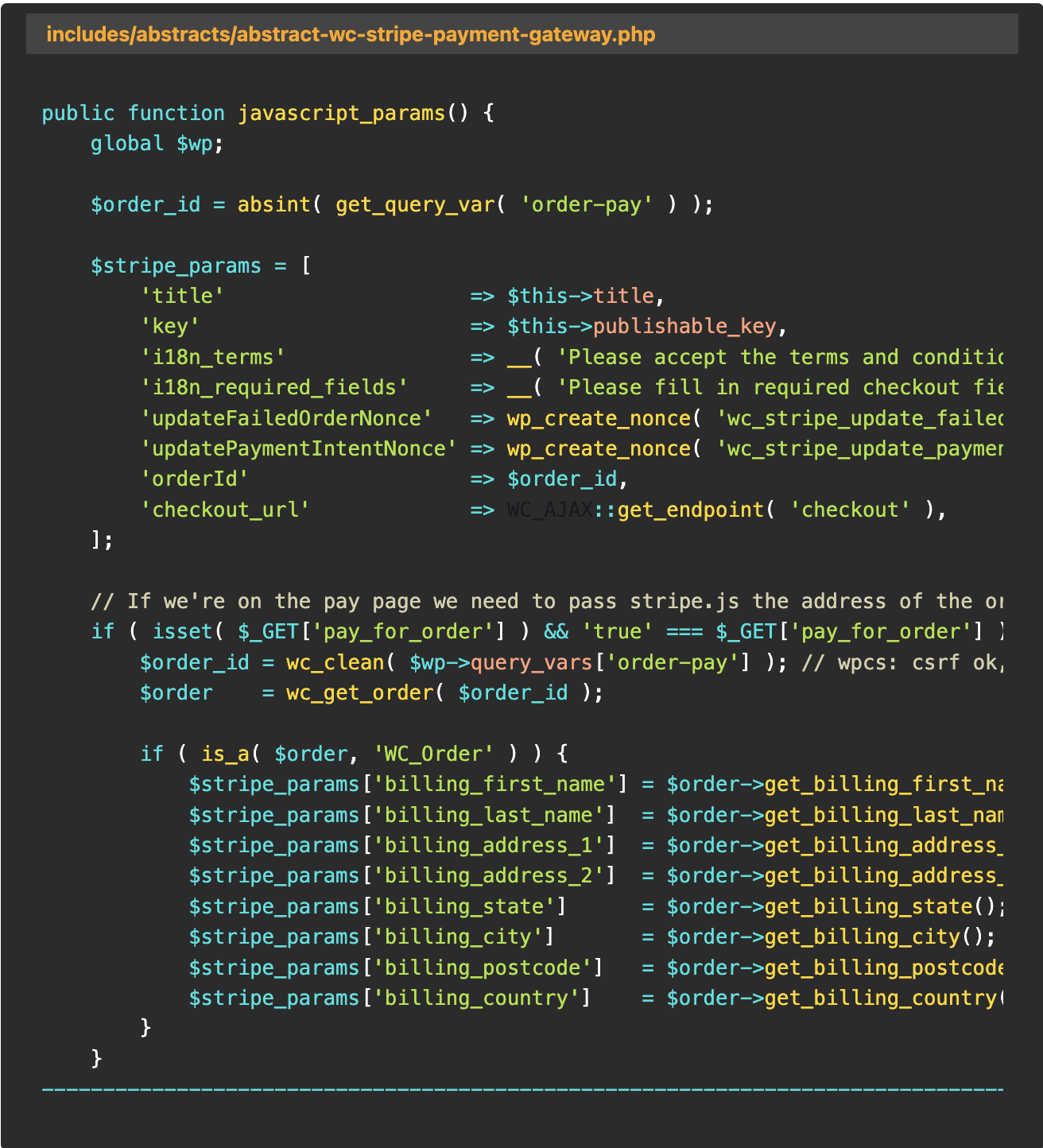
A threat actor can exploit the javascript_params and payment_fields function to retrieve sensitive information from the database, including Personally Identifiable Information (PII), email addresses, shipping addresses, and the user’s full name reported PathStack.
Exposure of the above data is considered serious and could lead to more attacks, such as scam emails that try to take over accounts and steal credentials.
Affected Products
WooCommerce Stripe Gateway Plugin version 7.4.0 and below
Fixed in Version
WooCommerce Stripe Gateway Plugin version 7.4.1
Vulnerability Details
The plugin’s ‘javascript_params’ and ‘payment_fields’ functions are vulnerable due to improper order object handling and a lack of access control mechanisms.
Due to these flaws in the code, any WooCommerce order information can be viewed by an unauthorized third party without first verifying the legitimacy of the request or the rightful owner of the order.
The necessary updates to address this flaw have been made available by WooCommerce. Users are advised to upgrade to version 7.4.1, which addresses this flaw.
Go to Source
Author: Guru








