
The Chinese-based Video surveillance equipment manufacturer has disclosed a critical flaw in their storage products, allowing cyber criminals to obtain admin permissions. This flaw can be exploited by sending specially crafted messages to the affected devices.
CVE-2023-28808: Improper Access Control in Storage Products
CVSS Score: 9.1
CVSS Vector : CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:N
Some Storage products, like Hikvision’s Hybrid SAN/Cluster storage, have an access control vulnerability that can be exploited by sending a specially crafted message to the affected devices.
Affected Versions:
| Product Name | Affected Versions | Download the Patch | User Manual |
| DS-A71024/48/72R | Versions below V2.3.8-8 (including V2.3.8-8) | Fixing Security Vulnerability of Hybrid SAN-230407.zip | User Guide for Fixing Security Vulnerability of Hybrid SAN_230410 |
| DS-A80624S | |||
| DS-A81016S | |||
| DS-A72024/72R | |||
| DS-A80316S | |||
| DS-A82024D | |||
| DS-A71024/48R-CVS | Versions below V1.1.4 (including V1.1.4) | Fixing Security Vulnerability of Cluster Storage-230407.zip | User Guide for Fixing Security Vulnerability of Cluster_230410 |
Source: Hikvision
To exploit this vulnerability, the threat actor must already have access to the network to send a specially crafted message to the affected devices.
How to Upgrade
Updates are available for all vulnerable devices. Hikvision has requested users use “Internet Explorer” to upgrade the version.
The download package is available for all the vulnerable products. The package consists of 4 files, as shown below.

To upgrade the version of the devices, users can follow the below steps.
Step 1: Log in to the webpage (http://<IP>:2004) of the device; go to System —> Tool to reach the upgrading page.
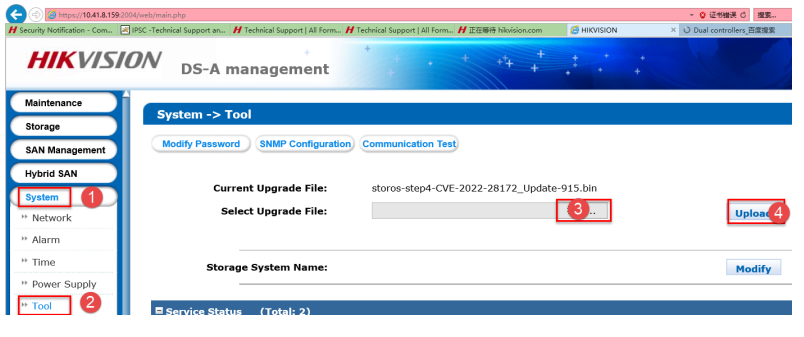
Step 2: Select upgrade as shown in the (3) picture and select “storos-step1-CheckMd5_for_CVR-V1.0-915.bin” from the downloaded package.
Note: Do not attempt to upgrade if the upgrade fails on the first attempt. Hikvision informed their users to contact the HK Technical Support team.
Repeat these upgrades for all available packages for the above-mentioned vulnerable products. For further information, kindly follow the steps to upgrade user-guide for Hybrid SAN and Cluster Storage from Hikvision.
Credits to the Vulnerability Reporter
This vulnerability was reported to Hikvision by an Indian Security researcher named Souvik Kandar from the Redinent Innovations team in India, along with the help of CERT-In.
Go to Source
Author: Guru








