Last week, OpenSSL issued a security update to address eight documented security flaws, including a high-severity bug (CVE-2023-0286) that can enable attackers to read memory contents or launch denial-of-service attacks. The vulnerability is expected to mostly impact applications with customized CRL retrieval functions. OpenSSL advises users to upgrade immediately. Additionally, seven moderate-severity issues were identified that require immediate attention.
According to an OpenSSL advisory, these include:
- A timing based side channel vulnerability (CVE-2022-4304) exists in the OpenSSL RSA Decryption implementation which could be sufficient to recover a plaintext across a network in a Bleichenbacher style attack. To achieve a successful decryption an attacker would have to be able to send a very large number of trial messages for decryption. The vulnerability affects all RSA padding modes: PKCS#1 v1.5, RSA-OEAP and RSASVE. “An attacker that had observed a genuine connection between a client and a server could use this flaw to send trial messages to the server and record the time taken to process them.”
- A read buffer overrun can be triggered in X.509 certificate verification, specifically in name constraint checking. The read buffer overrun (CVE-2022-4203) might result in a crash which could lead to a denial of service attack. “In theory it could also result in the disclosure of private memory contents (such as private keys, or sensitive plaintext) although we are not aware of any working exploit leading to memory contents disclosure as of the time of release of this advisory,” the group said.
The group also patched multiple memory corruption issues that exposes OpenSSL users to denial-of-service conditions.
Over Privileging on Cloud Apps
Over 90% of enterprises have committed to a multi-cloud strategy, which makes businesses more agile, flexible, and streamlined. However, complexity creates vulnerabilities where secrets leak out, and recent breaches at Microsoft and airports have made misconfigured S3 buckets a cybersecurity trope. Over privileging and access creep are just as dangerous and common. Cloud security posture management (CSPM) vendors use a mere 11% of the permissions they are granted, which shrinks to 5.3% across all users and roles.
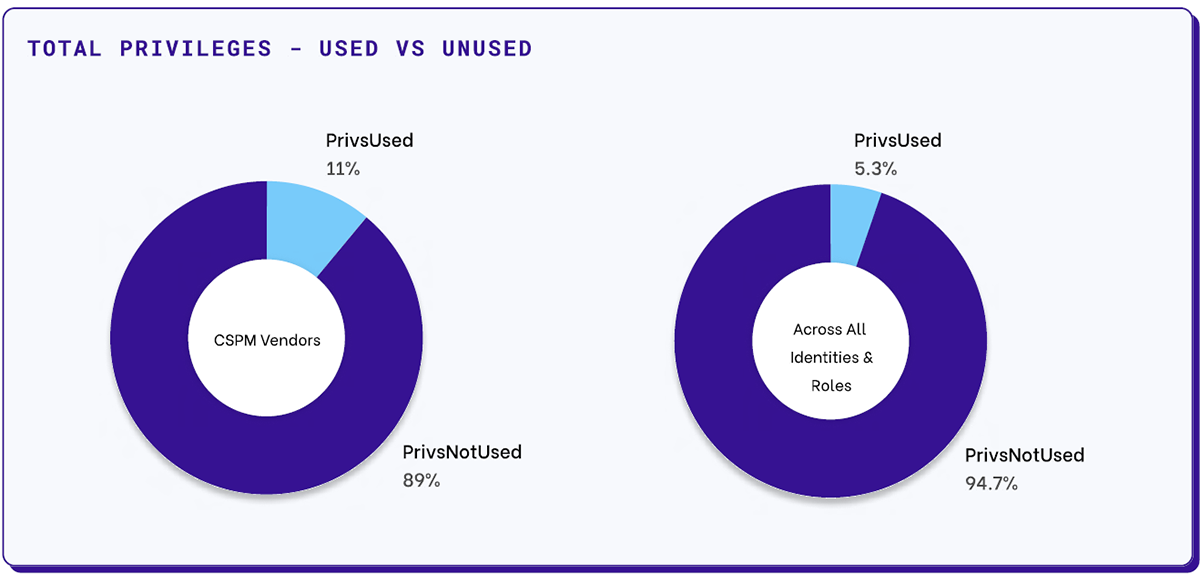
According to the Permiso team, secrets are often shared, rarely rotated, and long-lived, which makes them vulnerable. This is due to default permissions being allowed for machine identities, leading to a situation where threat actors only need access to one overly permissioned account to gain privileged access over much of the cloud.
To manage this risk, organizations need to audit permissions and establish strong IAM policies for all users, including machines, and determine what data an application needs access to and what it doesn’t. A software org chart can help trace access among apps and assign or restrict permissions.
Go to Source
Author: Ryan Naraine
Go to Source
Author: Dark Reading Staff, Dark Reading








