DNS security is critical in today’s world to protect against the growing threat of DNS attacks.
The risk of financial loss, data theft, and reputational damage increases for organizations that do not take DNS security seriously.
The Domain Name System (DNS) is a critical component of the internet that translates human-readable domain names (e.g., www.example.com) into IP addresses (e.g., 192.0.0.1) that computers can understand.
In the modern world, DNS is required because domain names are more straightforward for people to remember than IP addresses.
Without DNS, most people would find the internet experience difficult and unpleasant.
Deploy Secure Web Gateway (SWG) Protect your employees and critical resources from web-based attacks
DNS filtering and security techniques are required to address these issues while balancing censorship concerns.
87% of organizations experienced a DNS attack in the last year, up 8% from the year before, according to IDC’s 2021 Global DNS Threat Report.
Many of these attacks had severe consequences. According to the report, 76% of DNS attacks resulted in application downtime, and the average attack took more than five and a half hours to mitigate.
DNS filtering is useful for restricting access to websites and online resources based on predefined rules and policies.
It can enhance security, uphold compliance, enforce acceptable use guidelines, and manage bandwidth.
The DNSSEC (Domain Name System Security Extensions) protocol is used to improve DNS security, which adds digital signatures to DNS data to authenticate its origin and integrity.
Table of Contents
- What is DNS?
- DNS-over-HTTPS
- What is DNS filtering?
- Limitations and Considerations
- What does a DNS filter do?
- How does the DNS Filter block malicious domains?
- Difference between DNS Filtering and a Secure Web Gateway
- Key Difference
- Conclusion
What is DNS?
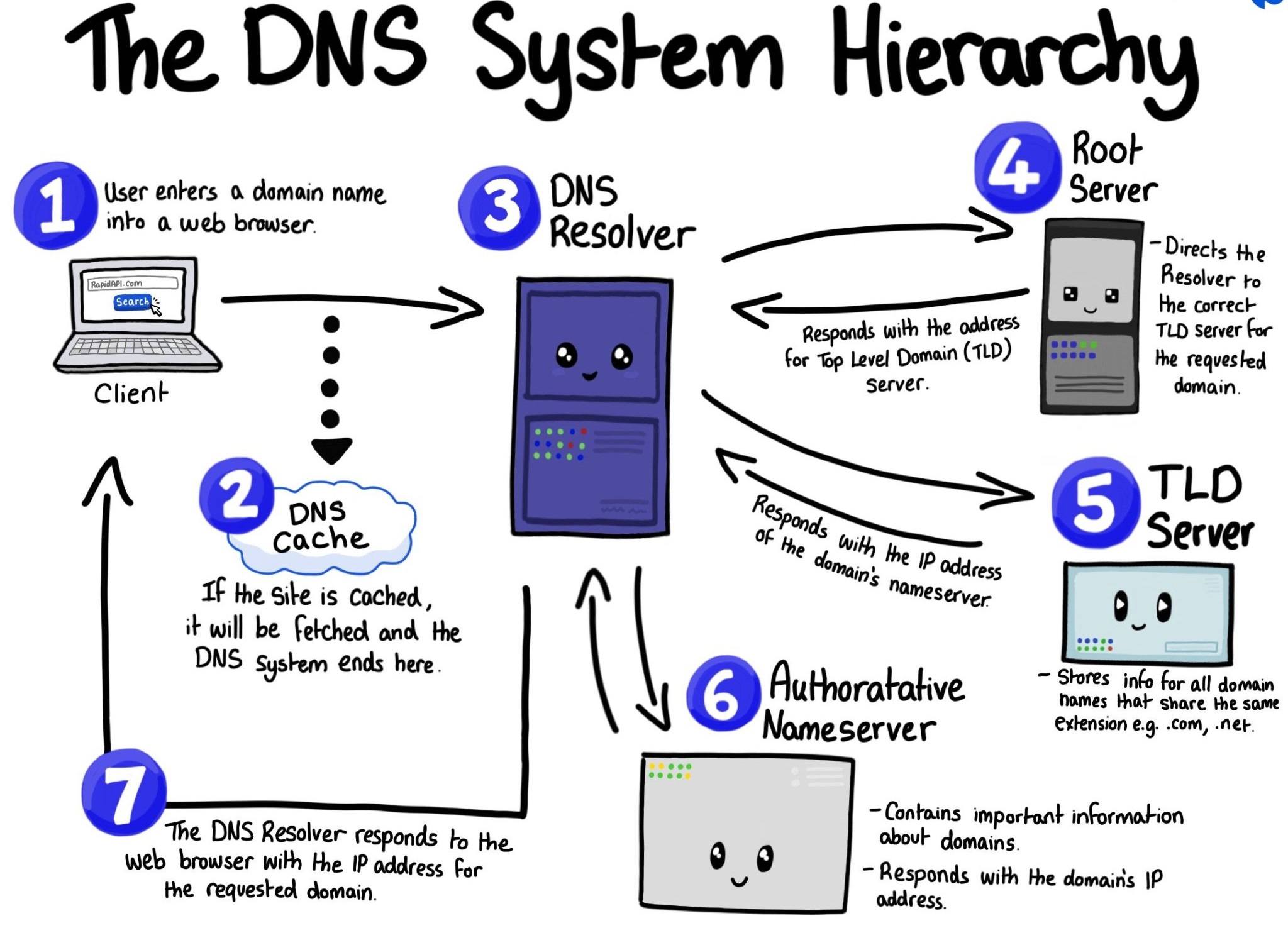
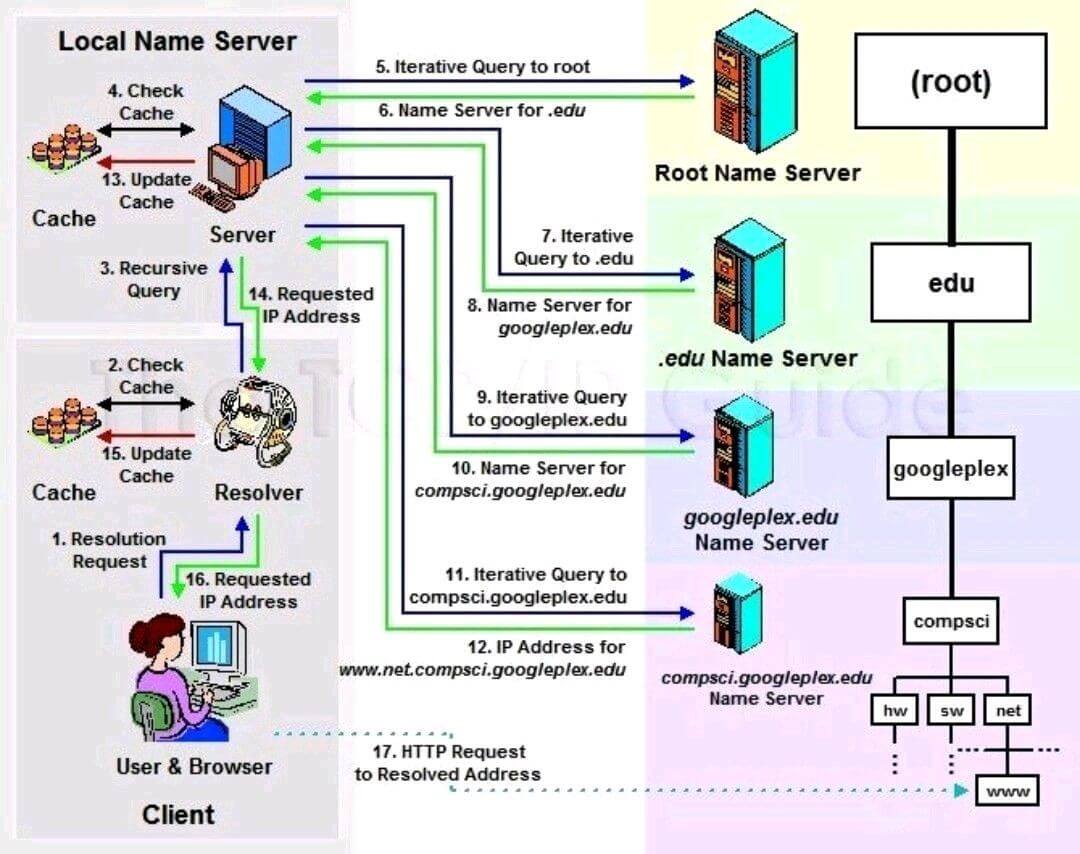
Humans find it easier to remember domain names, but computers and networks identify one another using IP addresses.
DNS translates domain names to IP addresses, so we can access websites using names instead of numbers.
DNS is a distributed database that contains mappings between domain names and IP addresses.
DNS servers spread all over the internet help perform the translation. It uses a hierarchy of DNS servers.
If one DNS server doesn’t know the IP address for a domain name, it asks for another higher-level DNS server.
The highest-level DNS servers are called root nameservers.
DNS is a critical component of how the internet works. Without DNS, we would have to access websites and servers by IP address which would be very difficult!
DNS attacks are common and can be dangerous. Some of the main types are:
DNS-over-HTTPS
DNS-over-HTTPS and DNS-over-TLS are also used to encrypt DNS traffic and prevent sniffing or manipulation.

Many public DNS services, like Google DNS, Cloudflare DNS, etc., provide better performance, security, and censorship resistance than ISP default DNS services.
But they can also log user data.
DNS stands for Domain Name System. It is a fundamental system that enables us to use practical domain names rather than IP addresses that we would otherwise have to remember.
DNS Poisoning
They manipulate DNS data to redirect users to malicious websites instead of the intended one. This can be used to steal data or install malware.
DNS Tunneling:
Using DNS queries to tunnel data and bypass firewalls. Attackers can use this to communicate with compromised systems.
DDoS Attacks:
Flooding DNS servers with huge DNS queries to overload them. This can make websites inaccessible.
DNS Hijacking
- It is the practice of rerouting a domain’s DNS requests to untrusted servers to steal information or launch attacks.
- This can be done by compromising DNS registrars, registries, or hosting providers.
- Multi-factor authentication and robust security controls can limit this risk.
DNS security refers to the measures taken to protect the Domain Name System (DNS) from attacks and ensure DNS data’s integrity, availability, and confidentiality.
A comprehensive DNS security strategy that includes measures such as:
- DNSSEC (Domain Name System Security Extensions): A set of extensions to DNS that provide cryptographic authentication of DNS data, ensuring that it has not been tampered with in transit.
- DNS firewalls: A firewall that filters DNS traffic and blocks requests from known malicious domains.
- DNS monitoring: Regularly monitor DNS traffic for signs of suspicious activity, such as unusual query volumes or traffic patterns.
- DNS hygiene: Regularly auditing and cleaning up stale or unused DNS records to reduce the attack surface.
What is DNS filtering?
DNS filtering is a technique to control or limit access to specific websites or internet services by filtering domain name requests.
It intercepts and analyzes DNS requests and either allows or blocks access based on predefined rules or policies.
DNS filtering can provide several benefits for organizations, businesses, schools, and even individual users:
- Security: DNS filtering can help protect against phishing attacks, malware, and other cyber threats by blocking access to known malicious websites.
- Content control: Organizations can use DNS filtering to enforce acceptable use policies and prevent access to inappropriate or distracting websites, such as adult content, social media, or entertainment sites.
- Bandwidth management: By blocking access to bandwidth-intensive websites or services, organizations can conserve network resources and ensure optimal performance for business-critical applications.
- Compliance: DNS filtering can help organizations meet compliance requirements by limiting access to specific types of content or ensuring that data does not leave the network.
Limitations and Considerations
While DNS filtering can be an effective tool for controlling internet access, it has some limitations and considerations:
False positives and negatives: DNS filtering relies on predefined rules and policies, sometimes resulting in false positives (blocking legitimate websites) or false negatives (allowing access to malicious or inappropriate websites).
Bypassing: Savvy users may bypass DNS filtering using VPNs, proxy servers, or alternative DNS resolvers. Organizations should consider implementing additional security measures to address these potential bypass methods.
Privacy concerns: Some users may have concerns about the privacy implications of DNS filtering, as it involves inspecting and potentially logging DNS queries.
Choosing a reputable DNS filtering service that respects user privacy and complies with relevant data protection regulations is essential.
What does a DNS filter do?
A DNS filter, also known as a DNS blocker or DNS-based web filter, is a type of content filtering technology used to prevent access to specific websites or types of content.
It works by intercepting requests made by a user’s web browser to resolve domain names into IP addresses and then filtering those requests based on rules or policies.
Organizations commonly use DNS filters to enforce acceptable use policies, protect against malware and phishing attacks, and prevent access to inappropriate or non-work-related content.
Parents can also use them to control their children’s access to the internet by blocking certain websites or categories of websites.
To understand how DNS filtering works, let’s first look at the standard process of a DNS query:
- Users enter a URL (e.g., www.example.com) into their web browser.
- The user’s device sends a DNS query to a DNS resolver, typically provided by their Internet Service Provider (ISP) or a third-party DNS service.
- The DNS resolver looks up the corresponding IP address for the requested domain name in its cache or queries other DNS servers if necessary.
- The DNS resolver returns the IP address to the user’s device.
- The user’s device connects to the web server hosting the website at the returned IP address, displaying the website’s content in the browser.
With DNS filtering in place, the process changes slightly:
- Users enter a URL (e.g., www.example.com) into their web browser.
- The user’s device sends a DNS query to the DNS resolver, which is now configured to use a DNS filtering service.
- The DNS filtering service intercepts the DNS query and checks the requested domain name against its filtering rules and policies.
- If the domain name is allowed, the DNS filtering service forwards the query to the DNS resolver, which continues the standard process of looking up the IP address and returning it to the user’s device.
- If the domain name is blocked, the DNS filtering service returns a false or blocked IP address to the user’s device, preventing access to the requested website.
How does the DNS Filter block malicious domains?
DNS filtering is an efficient and effective way to protect users from malicious content.
Additionally, DNS filtering should be used in conjunction with other security measures, such as firewalls, antivirus software, and intrusion detection systems, for a comprehensive security approach.
Here’s how DNS filtering works to block malicious domains:
- DNS Query:
- When a user tries to access a website, their device sends a DNS query to a DNS resolver, typically provided by their Internet Service Provider (ISP) or an external DNS provider like Google or Cloudflare.
- The query asks for the IP address corresponding to the website’s domain name.
- Filtering Rules: DNS filtering solutions maintain a database of blacklisted or suspicious domains known to be associated with malicious activities.
This database is often updated in real-time based on threat intelligence feeds, user submissions, and automated web crawlers that discover new malicious domains.
- Query Inspection:
- The DNS resolver inspects the query against the filtering rules.
- Suppose the requested domain is not found in the blacklist. In that case, the DNS resolver proceeds with the regular DNS resolution process, ultimately providing the user’s device with the IP address of the requested domain.
- Blocking Malicious Domains: If the requested domain is found in the blacklist, the DNS resolver will take one of the following actions:
- Return a “non-existent domain” (NXDOMAIN) response, indicating that the domain does not exist.
- Redirect the user to a “block page” or a “warning page,” informing them that the requested site has been blocked due to security concerns.
- Logging and Reporting: DNS filtering solutions can also generate logs and reports on blocked queries, allowing administrators to monitor and analyze DNS traffic and security events.
It’s essential to keep the filtering rules and blacklists up-to-date to maintain high protection against emerging threats.
Difference between DNS Filtering and a Secure Web Gateway
DNS Filtering
DNS filtering and Secure Web Gateway are security measures used to protect users and networks from malicious content and harmful websites.
They operate at different stages of the web browsing process and have distinct features.
It works by blocking access to malicious domains and IP addresses at the DNS level.
It intercepts DNS requests from clients and blocks the lookup of domains known to be malicious or unwanted.
This prevents the client from accessing those domains.
However, DNS filtering alone is not very effective. It can be circumvented easily using proxy servers or typing IP addresses directly.
Also, it does not inspect web traffic content and cannot block malicious files or botnets.
| Pros | Cons |
| Simple to implement and manage | Limited to blocking at the domain level |
| Lightweight and fast, as it operates at the DNS level | Can be bypassed by using alternative DNS servers, VPNs or proxy services |
| Provides basic protection against malicious websites and content | Does not inspect content or provide advanced threat protection. |
Secure Web Gateway
A secure web gateway, on the other hand, works at the web proxy level. It intercepts all web traffic from clients and inspects the content.
It can block malicious domains, files, and botnets and enforce web policies.
It enforces web policies like blocking certain file types, restricting streaming media, blocking gambling and pornographic websites, etc.
This provides better control and web activity monitoring.
Secure Web Gateway provides granular access control with user authentication. This allows applying different policies to different users and user groups.
These techniques, including URL filtering, content filtering, and malware detection, are used to analyze and block malicious web traffic.
They also provide SSL/TLS decryption, user authentication, and access control to ensure only authorized users can access the network.
| Pros | Cons |
| Provides advanced threat protection, including real-time content analysis and malware scanning | More complex to implement and manage |
| Inspects both HTTP and HTTPS traffic | This may introduce latency due to the additional processing and inspection |
| Can enforce granular security policies, such as access control and data loss prevention | Can be more expensive compared to DNS filtering |
| Provides detailed reporting and analytics |
DNS Filtering Key Fifferences:
- operates at the DNS level, secure web gateways operate at the application layer
- It only blocks by domain, secure web gateways can filter within domains and at the page/content level
- It provides little visibility or control, secure web gateways offer reporting, logging, and granular policies
- It is easier to bypass, secure web gateways are more comprehensive proxies into web traffic
It is a more focused approach that specifically targets known malicious domains and IP addresses, while a secure web gateway provides more comprehensive protection against a wider range of web-based threats
Conclusion
DNS filtering is an essential first line of defense for controlling web access and protecting networks.
Blocking malicious or unwanted domains at the DNS level prevents users from accessing websites that host spam, malware, phishing, or other threats.
DNS filtering is lightweight, easy to set up, and works with existing infrastructure.
Companies like Cloudflare, Cisco, Webroot, and OpenDNS offer DNS filtering services and solutions that are highly effective, affordable, and help reduce risks.
Though basic, DNS filtering provides an easy layer of security that should be part of any organization’s web access strategy today.
Go to Source
Author: Cybersecurity News Team